Cybersecurity threats are constant, and social engineering is one of the most effective tactics attackers use. Understanding how social engineering leads to phishing helps organizations and individuals defend against attacks.
What is Social Engineering?
Social engineering is a psychological manipulation technique used by cybercriminals to trick individuals into divulging confidential information or performing actions that compromise security. Instead of breaking code, social engineering exploits people, specifically their trust, fear, and habits.
The Connection Between Social Engineering and Phishing
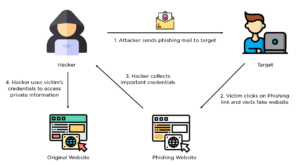
Phishing is the most widespread tactic that results from social engineering. It involves sending fraudulent messages that appear to come from reputable sources, often via email. These messages typically contain malicious links or attachments designed to steal sensitive information or install malware on the recipient’s device.
1. Research and Information Gathering
Cybercriminals begin by gathering information about their targets. This can include details about their job role, interests, and personal connections, often obtained from social media profiles or publicly available databases. The more information they gather, the more convincing their phishing attempts will be.
2. Building Trust
Attackers use personal details to impersonate trusted figures, increasing the chance the victim will respond. They might impersonate a colleague, a trusted vendor, or even a senior executive within the organization. By leveraging known relationships and authoritative figures, they increase the likelihood that the target will fall for the scam.
3. Exploiting Emotions and Urgency
Social engineers often create a sense of urgency or fear to prompt immediate action. Phrases like “Your account has been compromised,” or “Immediate action required” are common tactics used to pressure recipients into acting without thinking. Urgency prompts fast, uncritical decisions, which is exactly what attackers want.
4. Call to Action
The final step involves guiding the target towards a specific action, such as clicking on a link, downloading an attachment, or providing sensitive information. Once the target complies, the attackers achieve their objective, whether it’s harvesting login credentials, installing malware, or extracting financial information.
Real-World Examples of Social Engineering Attacks
1. Business Email Compromise (BEC)
A cybercriminal impersonates a company executive and sends an email to an employee in the finance department, instructing them to transfer funds to a specified account. The email appears genuine, complete with the executive’s email signature and writing style, convincing the employee to comply.
In 2021, Ubiquiti Networks, a global networking technology company, fell victim to a Business Email Compromise (BEC) scam, resulting in a $46.7 million loss. The attack was executed using CEO fraud, a common form of BEC where scammers impersonate high-level executives.
In 2016, Evaldas Rimasauskas defrauded Facebook and Google of over $100 million through a Business Email Compromise (BEC) scam. He impersonated Quanta Computer, a legitimate vendor, by creating fake email accounts and domains. Rimasauskas sent fraudulent invoices, directing payments to his accounts in Latvia and Cyprus. The scam went undetected for nearly two years due to the convincing nature of the emails and lack of verification. After discovery, he was arrested, extradited to the U.S., and sentenced to five years in prison. This case highlights the need for robust verification processes and employee training to combat BEC scams.
2. Spear Phishing
Unlike generic phishing attacks, spear phishing is highly targeted. For instance, an attacker might send an email to a specific individual within an organization, referencing a recent project or event. The personalized nature of the email increases its credibility and the likelihood of a successful attack.
Learn more about trap phishing
In June 2024, WazirX, one of India’s leading cryptocurrency exchanges, suffered a major cyber attack that significantly impacted its operations and users. Below is a detailed account of the incident:
Initial Breach: The attackers initiated the breach through a sophisticated spear-phishing campaign targeting key WazirX employees. These emails contained malware-laden attachments that, once opened, installed backdoors on the employees’ systems.
3. Social Engineering Vishing
Social engineering, specifically vishing (voice phishing), involves manipulating individuals into revealing confidential information over the phone. Attackers typically pose as legitimate entities, such as banks or government agencies, to create a sense of urgency and trust. They may ask for sensitive details like account numbers, Social Security numbers, or one-time passwords, exploiting the victim’s fear of fraud or other issues.
In 2020, scammers used vishing (voice phishing) to trick Twitter employees into revealing their login credentials by posing as IT staff. Gaining access to Twitter’s internal tools, attackers hijacked high-profile accounts (Elon Musk, Obama, Apple) and tweeted a Bitcoin scam, promising to double any money sent. Victims lost over $100,000 before Twitter intervened.
How the Attack Happened:
-
Vishing Attack on Twitter Employees
-
- Scammers called Twitter employees, posing as internal IT staff and claiming they needed help resolving security issues.
- Using social engineering tactics, they tricked employees into revealing their login credentials for Twitter’s internal systems.
-
Gaining Access to High-Profile Accounts
-
- With employee credentials, the attackers accessed Twitter’s admin panel, which allowed them to reset passwords and bypass security measures.
- They took control of accounts belonging to celebrities, companies, and influencers.
-
Executing the Bitcoin Scam
-
- Attackers tweeted from compromised accounts, claiming they were “giving back to the community” and that users who sent Bitcoin to a specified wallet address would get double their money in return.
- Many victims fell for the scam, sending over $100,000 worth of Bitcoin before Twitter could shut down the attack.
Protecting Against Social Engineering and Phishing
1. Education and Awareness
Training is essential because attackers target people, not just systems. Cybercriminals exploit human psychology, tricking individuals into revealing confidential information or performing actions that compromise security.
- Phishing Techniques: Awareness training should cover various forms of phishing, such as email phishing, SMS phishing (smishing), voice phishing (vishing), and spear-phishing. Train staff to spot suspicious links, question unexpected requests, and verify details using trusted channels. This training can include simulated phishing attacks to practice identifying and reporting fraudulent emails.
- Red Flags in Communications: Teach employees the warning signs of a phishing attempt, such as:
- Unusual sender addresses (e.g., misspelled domain names)
- Urgent requests or threats (e.g., “Your account will be locked unless you act now”)
- Unsolicited requests for sensitive information (e.g., passwords or personal data)
- Poor grammar or spelling errors in messages that appear official
- Verifying Unexpected Requests: Employees should always verify any unexpected requests, particularly those asking for money transfers, access credentials, or confidential data. This includes using a secondary communication channel (such as a phone call) to confirm requests before acting on them.
2. Robust Policies and Procedures
Clear, robust security policies can significantly reduce the risk of falling victim to phishing attacks and other social engineering schemes. These policies set expectations for how sensitive information should be handled and provide a structured framework for employees to follow.
- Handling Sensitive Information: Establish procedures that specify how sensitive data (like passwords, financial records, or personal identification) should be shared and stored. This may involve limiting access to such information to authorized personnel only and utilizing encryption for storing or transmitting sensitive data.
- Transaction Verification: Any financial or transactional request that could affect company assets should undergo multiple layers of verification. For example:
- When processing financial transactions, requesters should be required to follow an authentication process (such as multi-factor authentication).
- Use a second, independent communication method (e.g., calling a trusted number) to confirm transaction requests, especially if the request is unsolicited or involves large sums of money.
- Access Control and Least Privilege: Ensure that employees only have access to the information necessary for their roles. This reduces the chances of attackers obtaining sensitive data or credentials in case of a breach.
3. Technical Defenses
Advanced technical measures are critical for combating phishing and unauthorized access. These defenses rely on machine learning, domain verification, and multi-layered security protocols to protect users and systems. Here’s how they work:
Email Filtering Systems
Modern email security tools are designed to filter out phishing attempts before they reach employees’ inboxes. These systems use advanced techniques such as:
- Spam Filters: Detect and block known phishing emails based on predefined patterns.
- Machine Learning Algorithms: Analyze incoming messages for suspicious behaviors, such as unusual attachments, phishing links, or commonly used social engineering tactics.
- Domain Authentication: Verify that the sender’s domain matches the email’s claimed source using techniques like SPF (Sender Policy Framework), DKIM (DomainKeys Identified Mail), and DMARC (Domain-based Message Authentication, Reporting, and Conformance).
Multi-Factor Authentication (MFA)
MFA adds an extra layer of security by requiring multiple forms of verification. Key components include:
- Two-Factor Authentication (2FA): Combines passwords with one-time codes or biometric verification.
- Behavioral Analysis: Detects anomalies in login location or device usage to trigger additional verification.
Endpoint Protection Software
Endpoint protection safeguards devices by detecting and blocking threats. Key features include:
- Behavioral Analysis: Monitors device activity for unusual behavior, such as unauthorized file access.
- Real-Time Threat Detection: Scans files, applications, and processes to block malicious activity.
- Automated Response: Isolates devices or terminates malicious processes when threats are detected.
4. Incident Response Plans
A well-structured incident response plan is critical to minimizing damage during a phishing attack. Such a plan provides clear guidelines for detecting, containing, and resolving breaches effectively. Here’s how to create and implement an effective response plan:
Detection and Containment
The first step in any incident response plan is detecting the breach. This involves monitoring for signs of phishing activity, such as:
- Suspicious Emails: Unusual or unauthorized email activity, such as phishing emails sent from internal accounts.
- Unusual Logins: Failed login attempts or access from unfamiliar locations or devices.
- Unauthorized Data Access: Unexpected access to sensitive data or systems.
Communication and Notification
Effective communication is a key component of incident response. Relevant parties must be notified promptly, including:
- Internal Teams: Inform affected employees, IT teams, and senior management.
- Regulatory Bodies: Report the incident to authorities if personal data is compromised (e.g., under GDPR or CCPA).
- Customers or Clients: Notify affected individuals if their data was exposed, providing guidance on protective measures.
Forensic Investigation: Once the attack is contained, conducting a forensic investigation to understand the scope of the breach and determine how the attackers gained access is critical. This helps identify vulnerabilities in security procedures and systems, preventing future incidents.
Restoration and Recovery: After containment and investigation, the next step is restoring affected systems. This might involve resetting compromised credentials, applying patches to software vulnerabilities, and strengthening security measures. Additionally, any stolen or altered data should be recovered, and systems should be fully restored to normal operations.
Post-Incident Review: After the incident has been resolved, the organization should conduct a post-mortem to evaluate the response process, identify gaps in security, and learn from the incident. This allows the organization to strengthen defenses and improve incident response in the future.
Cybercriminals use social engineering to bypass technical defenses by manipulating people. By understanding the tactics used and implementing comprehensive security measures, organizations can significantly reduce their vulnerability to these threats. Remember, in the realm of cybersecurity, the human element is often the weakest link – but with proper training and vigilance, it can also become the strongest defense.





