Dark web threat intelligence refers to the process of collecting, analyzing, and acting on information gathered from the dark web to identify emerging risks before they become active threats. By uncovering early indicators of compromise (such as leaked credentials, exploit chatter, or mentions of a company’s assets) organizations gain a critical advantage in anticipating and preventing attacks.
To understand how this intelligence is gathered and applied, it helps to look at how dark web threat intelligence tools collect and analyze data in real time.
How Dark Web Threat Intelligence Works
Because the dark web is intentionally hidden, organizations depend on specialized tools and automated crawlers to detect and track potential threats. These systems identify compromised credentials, stolen financial data, and other sensitive information before attackers can exploit it.
1. Data Collection Across the Dark Web
Threat intelligence platforms continuously scan diverse sources, including ToR (The Onion Router) and I2P (Invisible Internet Project) networks, IRC and Telegram channels, criminal marketplaces, forums, and paste sites where stolen data is shared.
Learn more about why scammers use telegram
Using machine learning and natural language processing, these systems collect, categorize, and cache data in real time, allowing analysts to monitor developing threats and track malicious activity across multiple ecosystems.
2. Intelligence Analysis
Once data is collected, it’s analyzed to extract context and meaning. Security teams identify references to corporate credentials, intellectual property, or internal systems to assess the level of exposure and potential risk.
Analysts also evaluate the credibility of each source and the context in which the data appears, filtering signal from noise to ensure genuine threats are prioritized over false positives.
3. Actionable Insights and Response
Effective dark web threat intelligence starts with collection, and continues by driving action. Automated alerting and response playbooks allow security teams to trigger countermeasures such as forced password resets, domain takedowns, or access blocks.
Integration with SIEM and SOAR platforms helps teams operationalize dark web intelligence, aligning it with broader incident response and threat-hunting workflows.
Why Dark Web Threat Intelligence is Essential
Beyond the basics already discussed, dark web threat intelligence provides a number of benefits.
1. Early Warning for Targeted Attacks
Monitoring illicit activity such as phishing kits, malware, and exploit discussions allows organizations to predict cybercriminal behavior and take proactive steps to strengthen their defenses. Threat actors often discuss upcoming attacks in dark web forums, providing valuable intelligence that security teams can use to prepare for potential threats.
2. Protection Against Data Breaches
Stolen credentials and personal data frequently appear on the dark web, where they are bought and sold by cybercriminals. Organizations that actively monitor these transactions can respond swiftly to prevent unauthorized access, fraud, and identity theft.
Dark web threat intelligence serves as an early warning system, allowing businesses to take preventive measures before their sensitive information is exploited.
3. Compliance and Regulatory Requirements
Industries with strict data protection laws, such as GDPR and HIPAA, require organizations to ensure that sensitive information is not leaked. Failure to comply with these regulations can result in significant fines and reputational damage. Dark web threat intelligence aids in compliance by providing alerts on potential violations, enabling organizations to take corrective action and avoid legal repercussions.
Choosing the Right Dark Web Solution
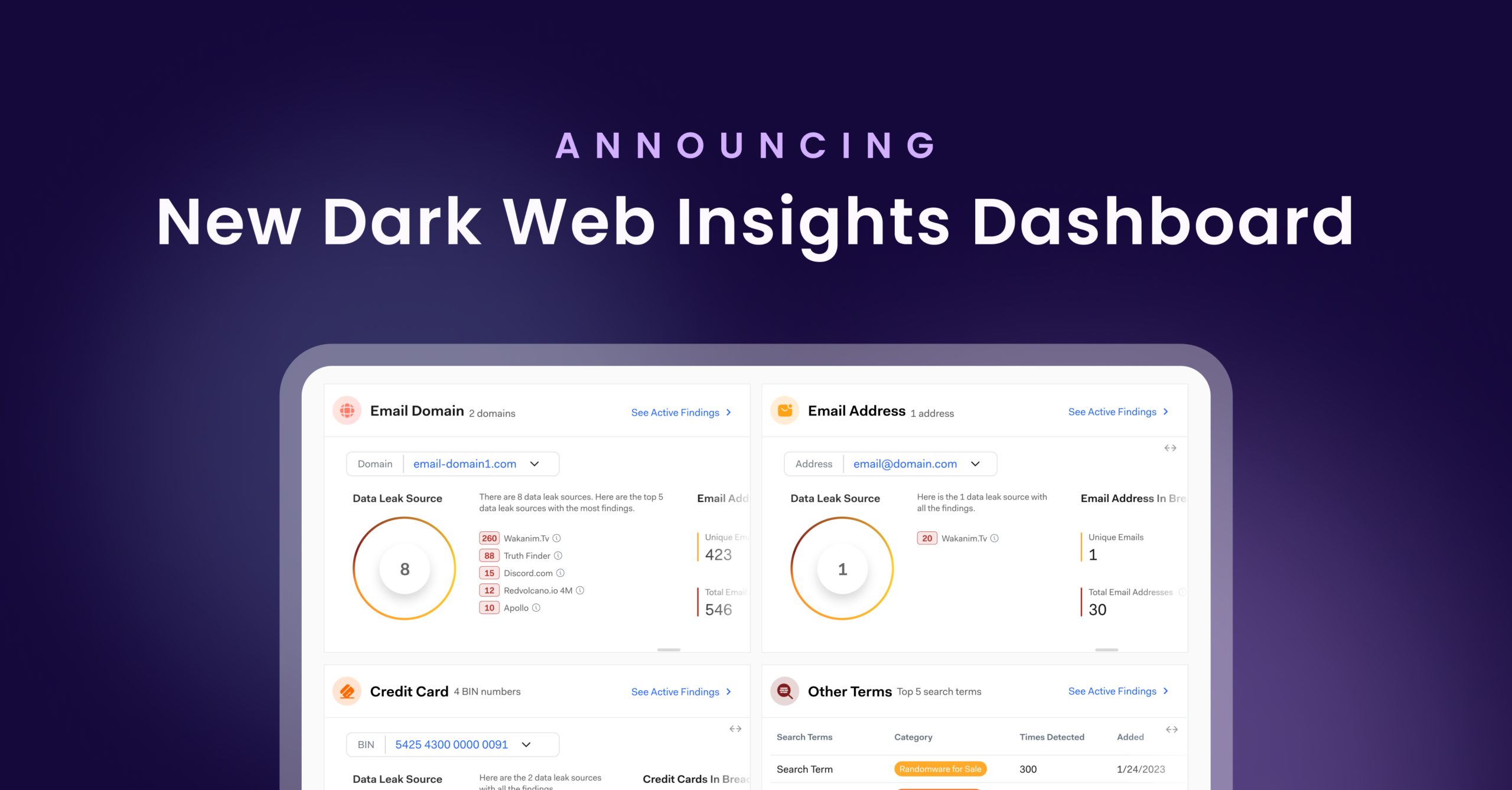
Bolster’s dark web monitoring solution provides businesses with real-time visibility into threats, leveraging AI and machine learning for accurate intelligence. Organizations benefit from deep and dark web coverage, scanning ToR, I2P, criminal forums, Telegram channels, and more.
A user-friendly dashboard offers stunning visualizations, making it easier to analyze threats and take action. Plus, risk-based insights prioritize critical threats, while automated playbooks allow organizations to implement predefined response actions such as alerting security teams or resetting compromised credentials. Seamless integration with SIEM/SOAR platforms enhances existing cybersecurity operations, enabling a more comprehensive approach to threat mitigation.
Request a demo of Bolster’s domain monitoring software today or start with a customized Domain Risk Report to uncover potential dark web threats to your organization.