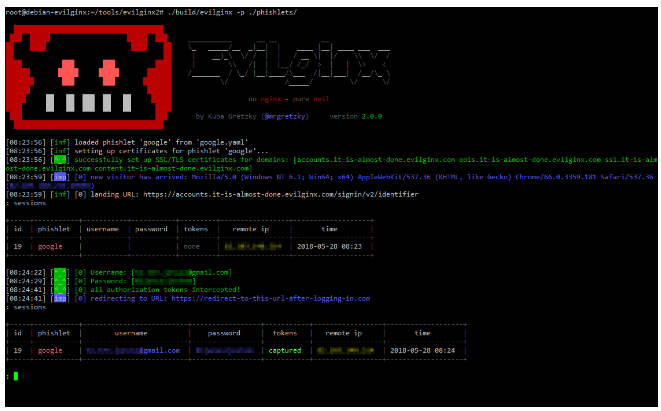
Scammers want you to use Telegram because it gives them…
107 results for keyword "Tips & Guides"
Exploring the Similar Worlds of Natural Language Processing (NLP) & Generative AI
Natural Language Processing (NLP) and Generative AI are reshaping cybersecurity,…
6 of the Best Anti-Phishing Software Choices to Protect Your Business
Phishing and online scam sites have become exceedingly sophisticated in…
Defining Subdomain Hijacking & How to Identify Subdomains at Risk
What is Subdomain Hijacking? Subdomain hijacking is an attacker having…
AI-Powered Fraud Detection 101: How to Uncover Cyber Attacks in 2025
Businesses are under constant pressure to stay ahead of digital…
How to Conduct a Website Takedown (The Hard Way), and How to Improve
If your business has any kind of digital presence in…
2025 Brand Protection Strategies: 12 Methods to Combat Evolving Digital Threats
Brand protection strategies need to evolve as quickly as the…
How to Avoid Fake CAPTCHA Scams That Initiate Malware
Online security measures like CAPTCHAs (Completely Automated Public Turing test…
The Click That Stole Holidays: Black Friday and Cyber Monday Scams Unmasked
The onset of Cyber Monday and Black Friday deals is…
Phishing & Online Scams Targeting the 2024 Election
As the 2024 U.S. presidential election draws near with discussions,…