Diamond Model of Intrusion Analysis is a simple yet…
107 results for keyword "Tips & Guides"
Everything You Need To Know About Email Spoofing
What is Email Spoofing? Email spoofing is a…
Identifying SSL Certificate Scams & Importance of Monitoring for Brand’s Identity
Phishing and scam websites often use SSL certificates to…
Can You Get Scammed on Telegram? Yes, Here’s How.
Telegram promotes itself as a fast, modern cloud-based messaging platform…
What Is Domain Spoofing and How to Stop It
What is Domain Spoofing? Domain spoofing is a type…
Top 5 Ways to Protect Customers this Holiday Season
Every year, Bolster research labs not only finds a…
Best Strategies For Stopping Business Email Compromise (BEC) Scams
Business Email Compromise scams are a surging problem that…
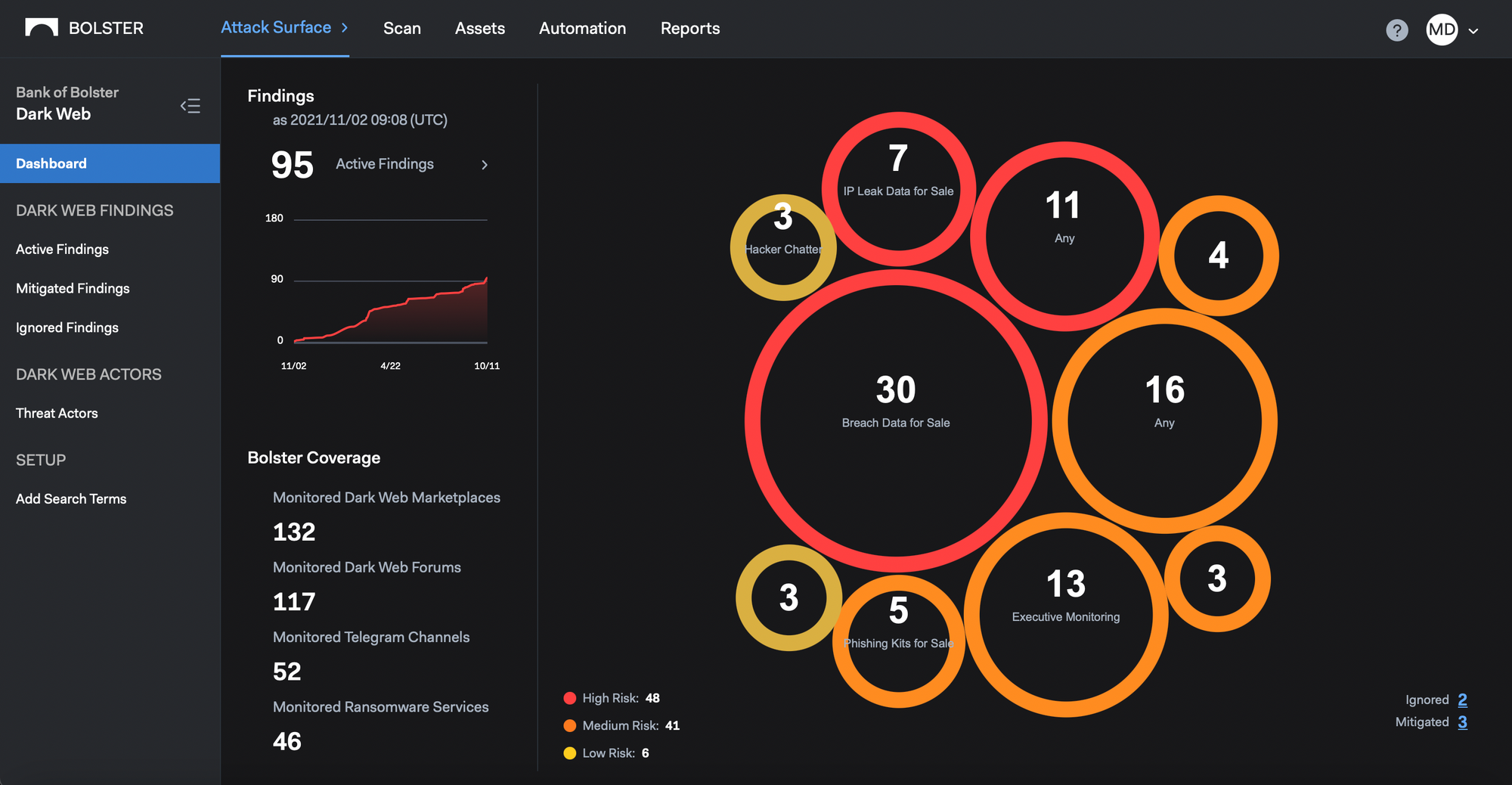
Protecting Customers in the Dark Web and Around the Clock
At Bolster, it has always been our mission to…
Navigating the Rise of Social Media Breaches
When more than half the world’s population uses social…
What is Vishing and Is It a Threat to Your Business?
What Is a Vishing Attack, and What Does It…
Everything You Need to Know About Digital Risk Protection
For modern organizations operating in the digital economy, protecting…