Cybersquatting, a form of domain name abuse, refers to…
18 results for keyword "Domain Protection"
How to Find Similar (Lookalike) Domain Names
Lookalike or “similar” domains are fraudulent domains that mimic…
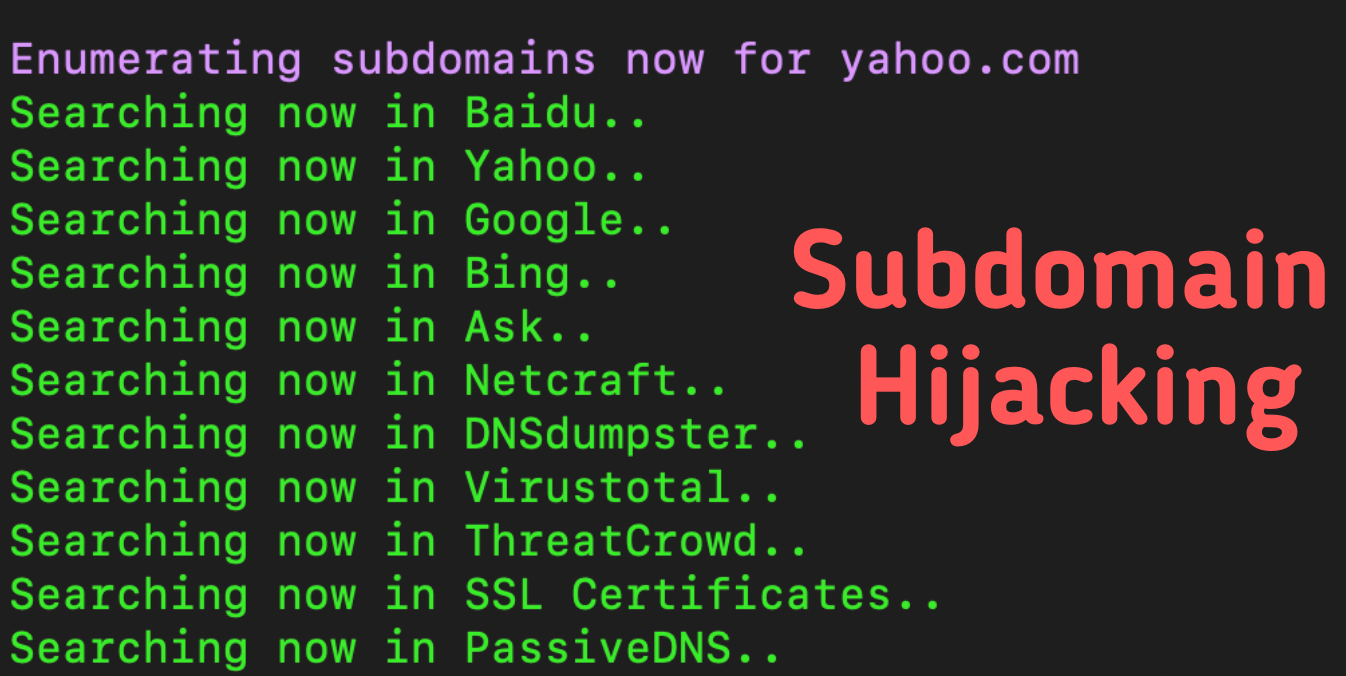
Defining Subdomain Hijacking & How to Identify Subdomains at Risk
What is Subdomain Hijacking? Subdomain hijacking is an attacker having…
How to Conduct a Website Takedown (The Hard Way), and How to Improve
If your business has any kind of digital presence in…
Understanding Domain Reputation Attacks and How to Protect Your Brand
Without even defining the term, you could probably guess that…
The Full Guide to Protecting Yourself from Fake Sale Websites
Online shopping is no longer a hot trend or something…
Digital Risk Monitoring Importance is Growing Faster Than Ever
In a digital landscape that seems to be changing daily…
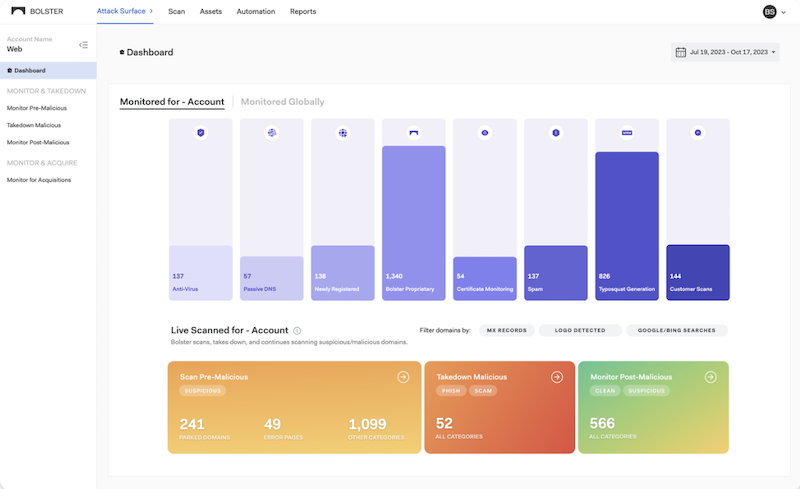
A Visual Journey: Exploring the Redesigned Bolster Dashboard
One of the top challenges that security practitioners often…
The Power of Automated Domain Monitoring
Today, business owners around the world understand that digital…
The Build vs. Buy Dilemma with Domain Risk Management
Domain risks are growing increasingly aggressive, and detrimental to businesses…
Evaluating Web Scraping, Crawling, and Automation with NodeJS Libraries
This blog is part 1 of a web scraping…
How to Conduct a Website Takedown In 3 Easy Steps
Malicious website domains are a headache for organizations to…