Image similarity has emerged as one of the most powerful…
38 results for keyword "Research"
Identifying Compromised Antivirus Software & Fake Sites
Antivirus vendors have significantly been impacted by the latest phishing…
Dissecting the Phishing Kit behind the Axis Bank Reward Points Campaign
Phishing campaigns targeting banking and financial institutions have always been…
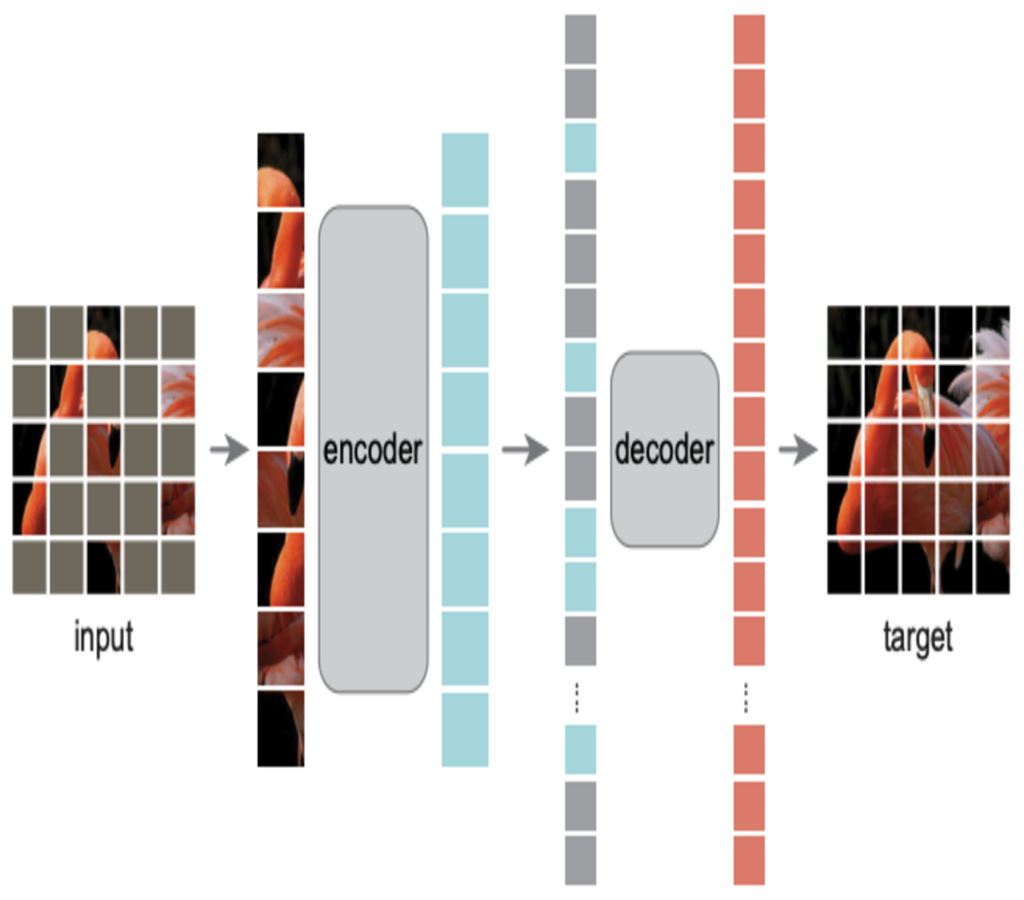
What is VIT-MAE? Scalable Learning for Vision Transformers.
Unprecedented gains in hardware capabilities and model sizes have compelled…
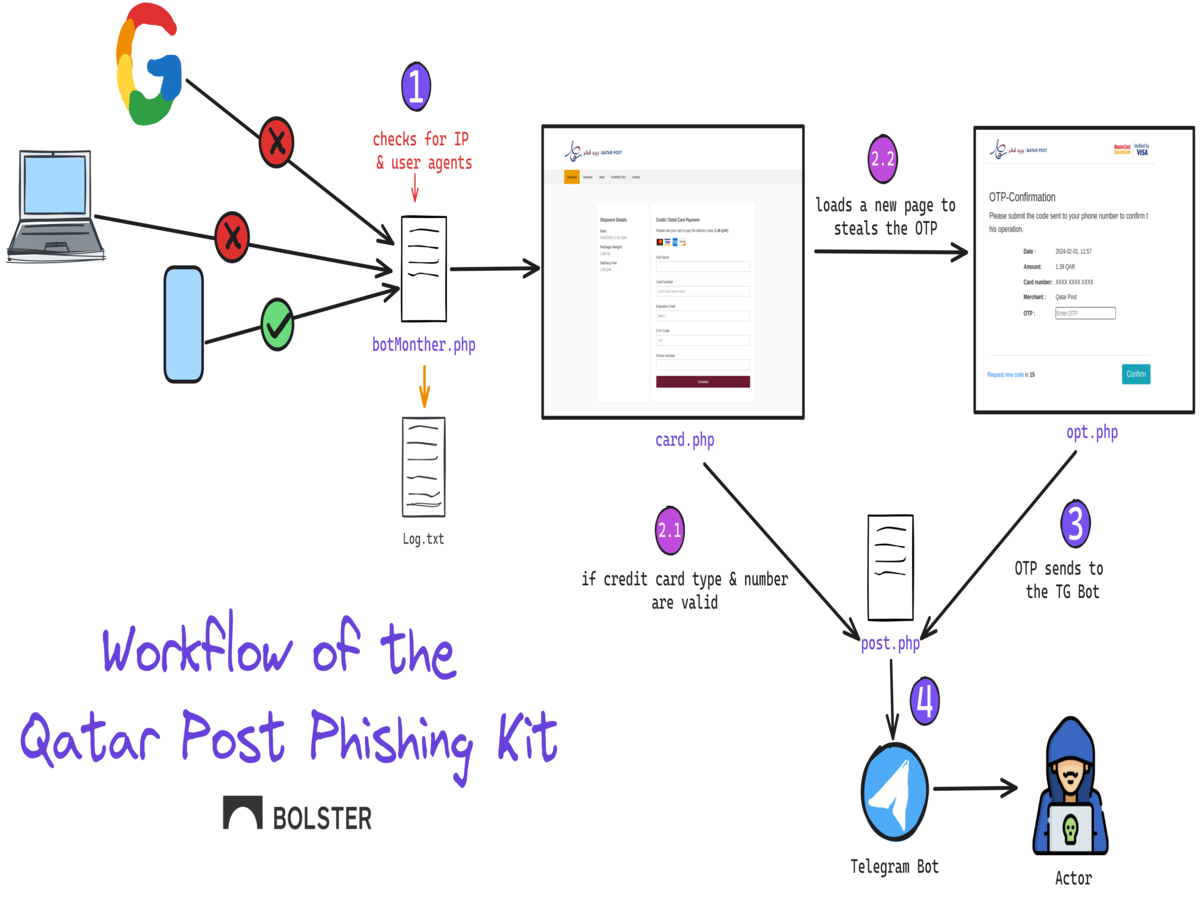
Dissecting the Newest Phishing Kit Targeting the Qatar Post
Name brand postal services have been increasingly targeted by phishing…
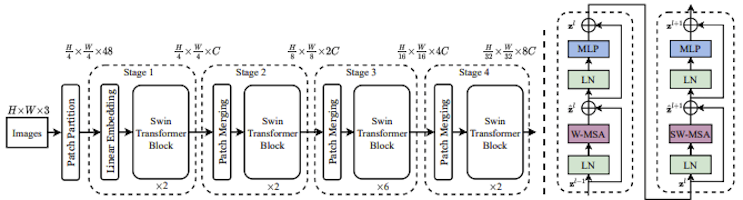
SWIN Transformers Explained: The Best of Two Worlds
A Swin Transformer is a vision transformer architecture that processes…
ICC World Cup 2023: Unmasking the Scams and Threats Targeting Fans Worldwide
The ICC World Cup 2023, the 13th edition of…
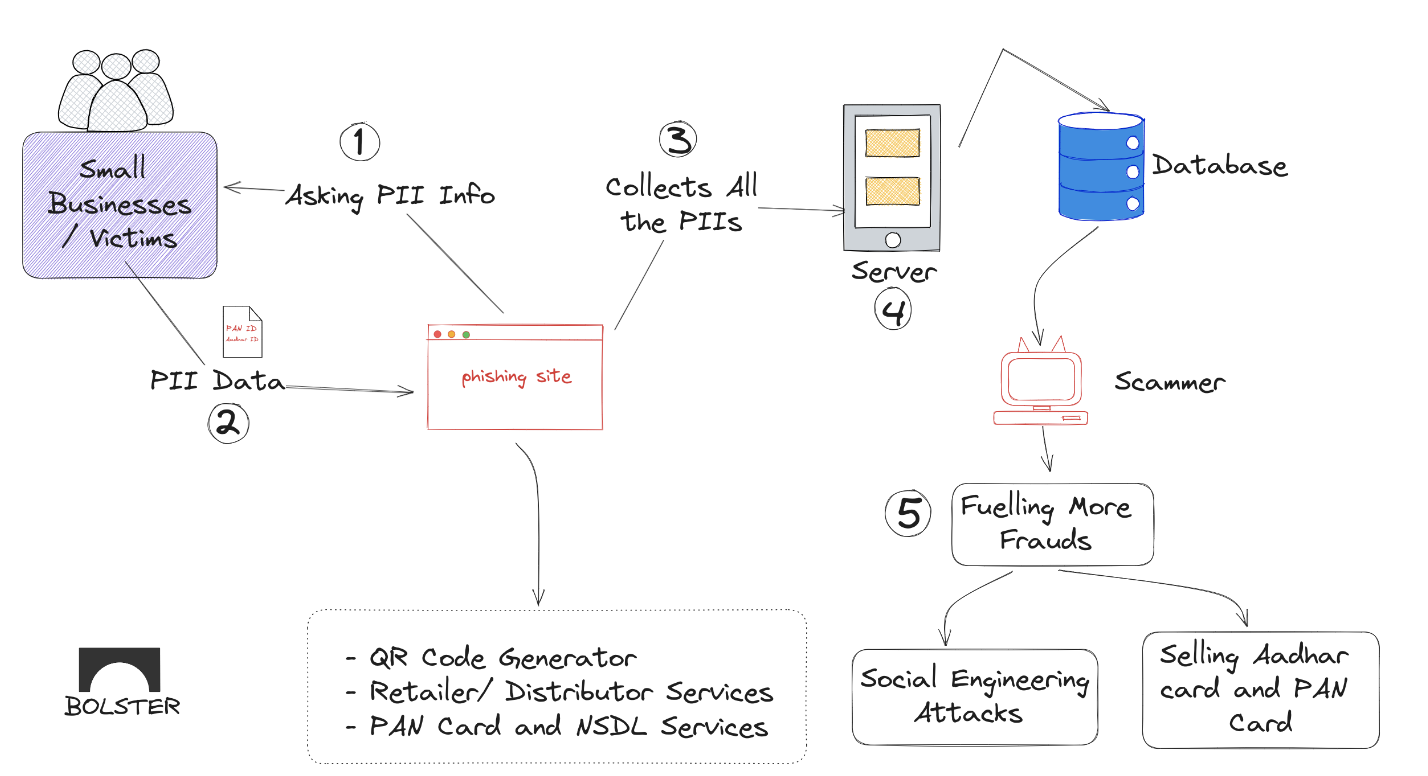
Under the Radar: Phishing Websites Masquerading as UPI Gateways to Secretly Steal Customer Data
Many threat actors are moving away from utilizing brand…
Empowering Brand Protection: Large Language Models and Their Role in Webpage Intent Identification for Brand Safety
Pattern recognition is a key skill that has enabled…
A Guide to the Diamond Model of Intrusion Analysis
Diamond Model of Intrusion Analysis is a simple yet…
The Best 5 Brand Protection Software Solutions in 2023
Suppose you have searched for ways to protect your brand…