Bolster vs. Competitors Bolster AI ZeroFox Automated Takedown < 24…
44 results for keyword "Brand Protection"
Detecting Deepfakes—How They Are Created & How to Spot Them
Deepfakes can be detected by looking for telltale signs such…
Gray Market vs. Black Market: 5 Ways to Protect Your Business
The gray market and the black market are similar in…
Six Impersonation Attack Examples and How to Shield Your Business
Impersonation attacks are smarter and more deceptive than ever, with…
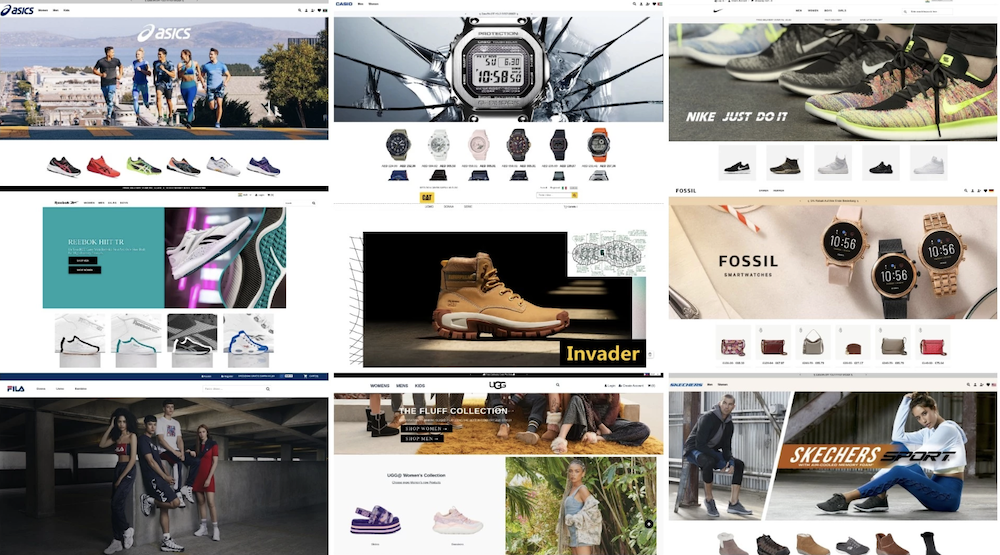
How a Massive Brand Impersonation Scam Campaign Targeted Popular Apparel Brands
Back in 2023, Bolster’s threat research team uncovered a widespread…
2025 Brand Protection Strategies: 12 Methods to Combat Evolving Digital Threats
Brand protection strategies need to evolve as quickly as the…
Weekly News Roundup: Ransomware Skyrockets, Proofpoint Phishing Emails, and More
This week, we’ve seen some big headlines in terms of…
Proactive Defense Against BEC Attacks: How to Stay Ahead of the Scammers
Business Email Compromise (BEC) has become a significant threat to…
The Need for AI Threat Detection in the Modern Cybersecurity Landscape
Today’s cybersecurity landscape demands much more than traditional threat detection,…
Ad-ventures: Investigating the Misuse of Google Ads in Malvertising Campaigns
In the sprawling extent of the internet, Google Ads has…
Digital Risk Monitoring Importance is Growing Faster Than Ever
In a digital landscape that seems to be changing daily…