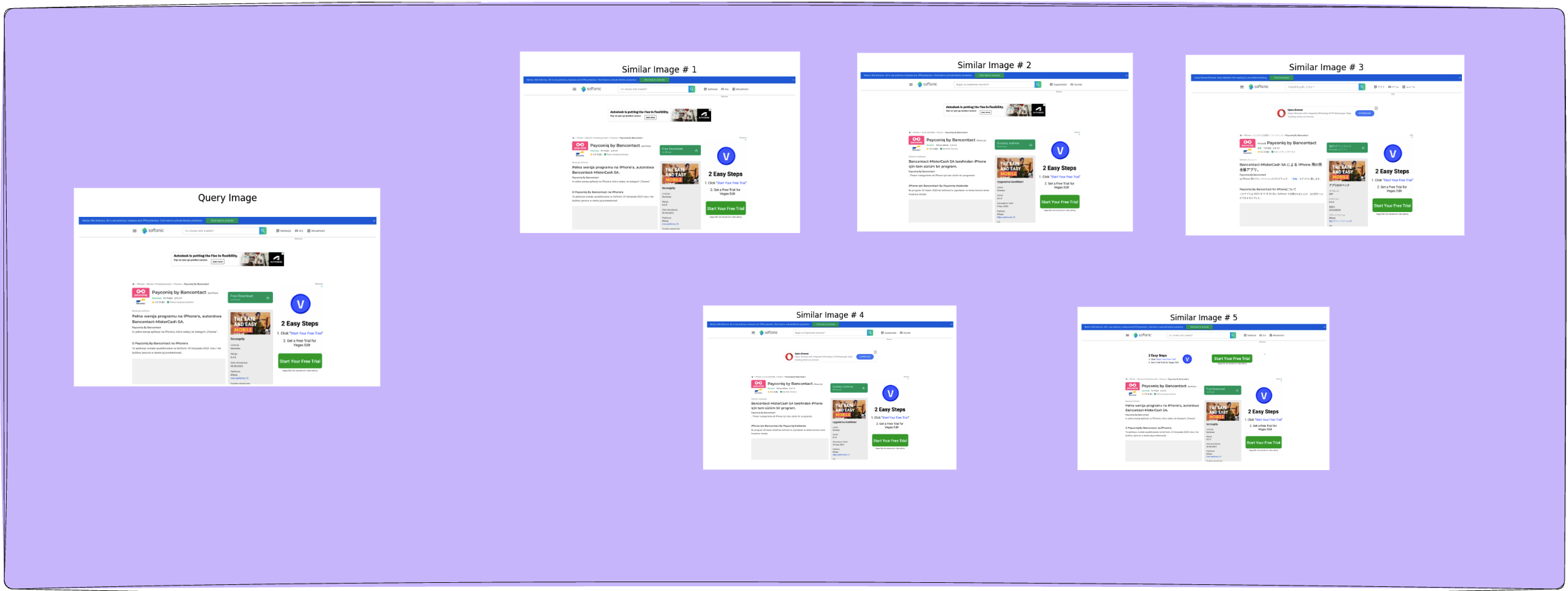
Image similarity has emerged as one of the most powerful…
44 results for keyword "Brand Protection"
Beyond Hashing: The Future of Anti-Phishing is Image Similarity Search
Computer vision modules are a critical component in a cybersecurity…
Using LLM’s for Heightened Cybersecurity: Supercharging Automated Takedowns With GPT
It takes a lot to surprise engineers working on…
Brand Impersonation Attacks: Which Industries are Most at Risk?
In late 2022, American Express was at the center…
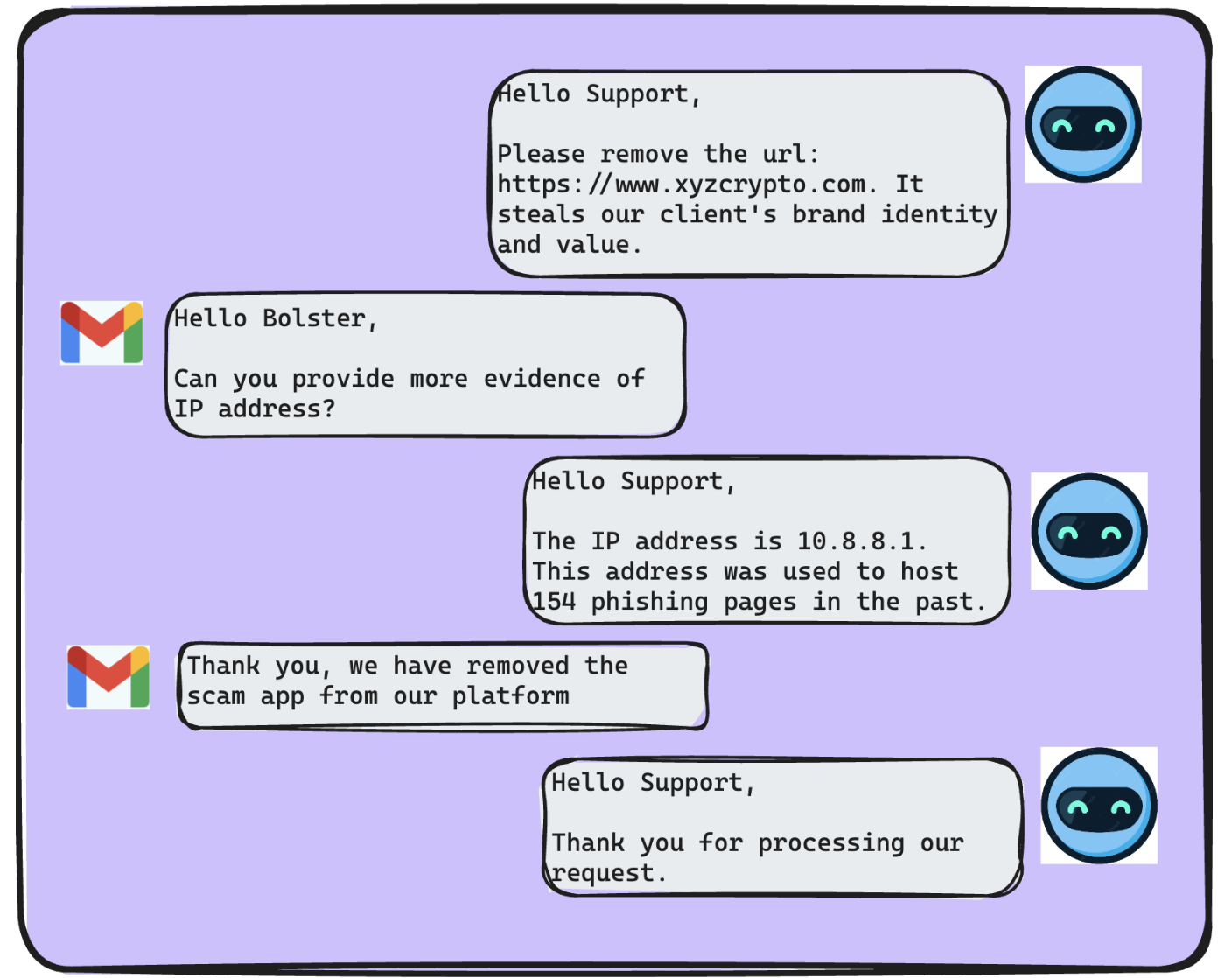
Automating Multi-Touch Takedowns with Large Language Models at Scale
As part of our Large Language Models at work…
5 Ways to Protect Your Business Against Executive Impersonation Scams
There’s no doubt social media cyber risk attacks are…
What Are Executive Impersonation Attacks, and What Do They Look Like?
Cybercriminals keep coming up with new methods to deceive…
What’s Brand Protection Got to Do with External Attack Surface Management?
External attack surface management (EASM) encompasses a wide variety of…
Definitive Guide to Modern Brand Protection
Businesses are relying more and more on digital assets…
Phishing in the Metaverse: The New Reality of Brand Protection
The metaverse promises a new level of immersion and…
Copyright Infringement Examples: Lessons to Help You Protect Your Business
Copyright infringement is a fairly common technique for cyber criminals…
Real-world Phishing Attack Highlights Why Every CISO Needs to Protect Against Brand Impersonation
When researchers from Armorblox discovered a phishing attack from…