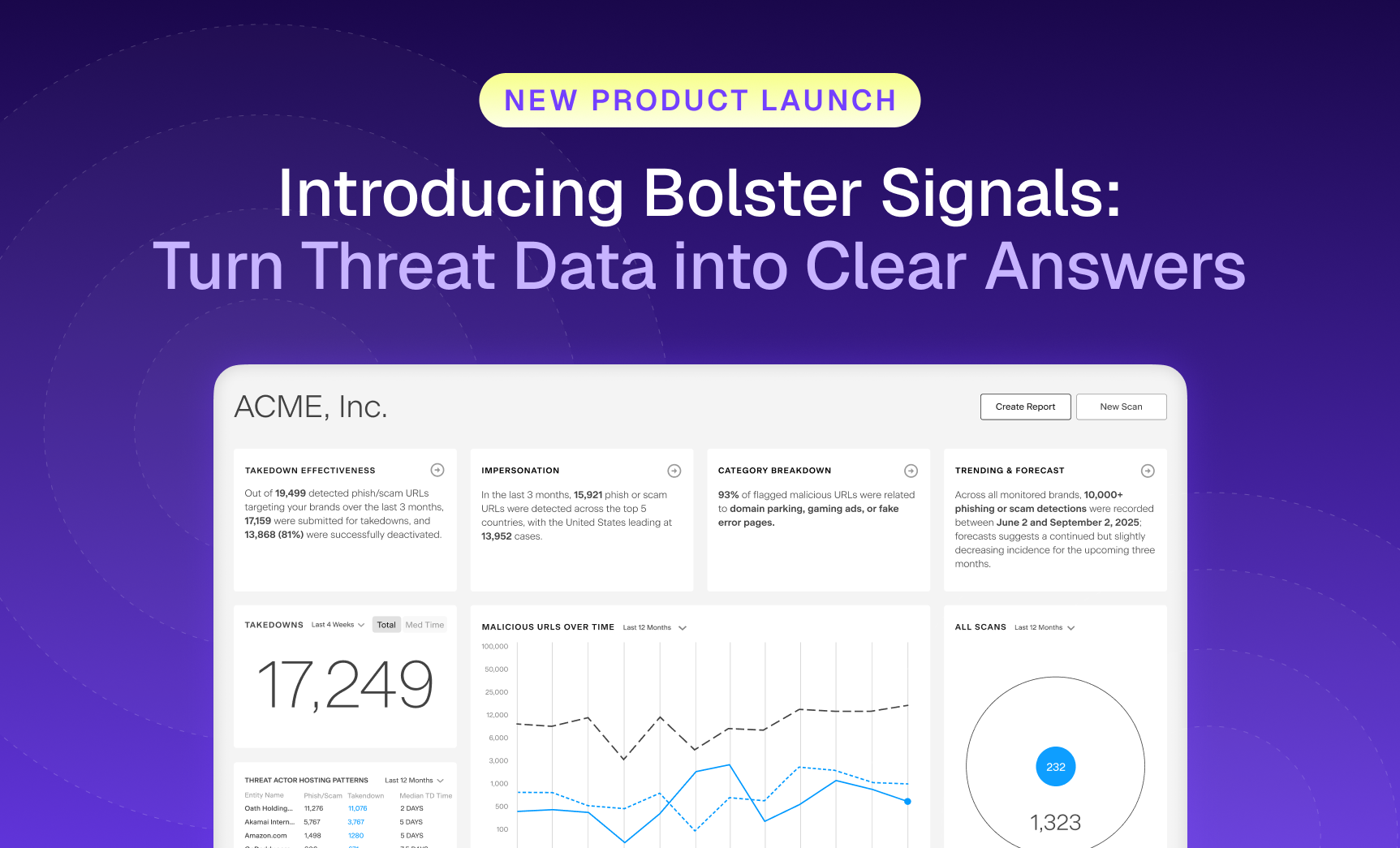
Security teams are flooded with more threat data than ever, and still struggle to see what matters most.…

The Bolster Blog
Thought provoking blogs discussing recent trends on digital risk protection services, phishing protection, threat intelligence, artificial intelligence, machine learning, brand protection and more!
Recent Posts
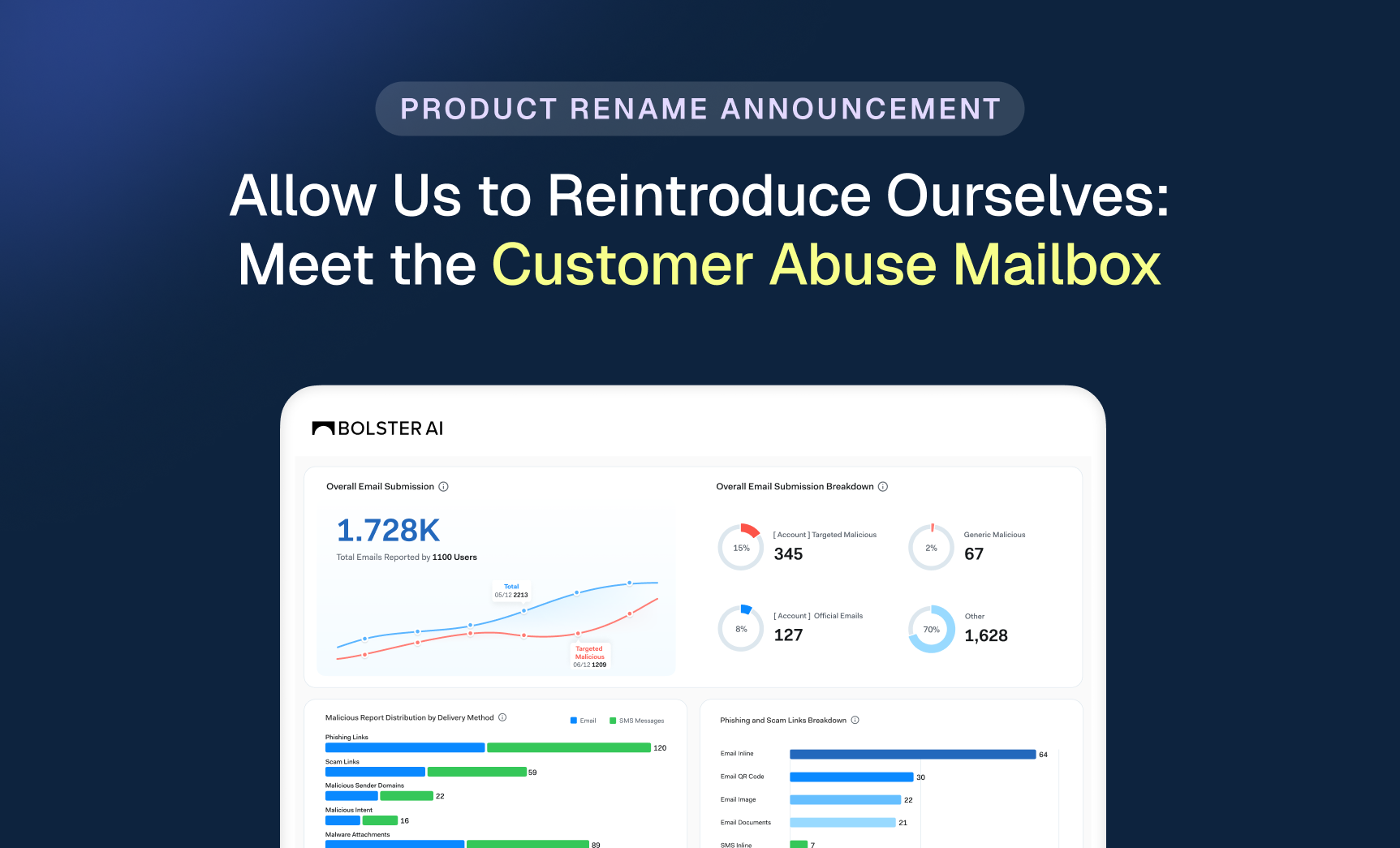
Allow Us to Reintroduce Ourselves: Meet the Customer Abuse Mailbox
Let’s clear something up. For a while, we referred to one of our most impactful features as “AI Security for Email.” While accurate in some.
Why AI-Generated Phishing Pages Are Harder to Detect (and How Bolster Stops Them)
Imagine clicking on what looks like your bank’s login page. The logo is crisp, the URL seems harmless at first glance, and even the support.

Buyer’s Guide: Purchasing a Brand Security Solution
Your brand is constantly under attack. To stay protected, you need an AI-powered brand security solution that keeps up with today’s AI-driven threats. Not sure what to look for? Use the Bolster AI Buyer’s Guide to evaluate your options.
Best Phishing Email Tools: Detection & Automated Takedowns
Phishing attacks cost organizations an average of $4.88 million per…
Advanced Threat Protection Solutions: Stopping Attacks Before They Start
Cyber attacks are surging at an unprecedented pace. According to…
Detect and Kill AI Phishing: A 6-Step Defense Guide
The phishing landscape has transformed dramatically. What once required manual…
Call Forwarding Scams & How to Protect Yourself from Dangerous Fraud
Call forwarding scams are an increasingly common form of fraud…
7 Tips to Prevent Cybersquatting Before It Damages Your Brand
Cybersquatting, a form of domain name abuse, refers to…
How to Safely Open a Suspicious Link in 5 Steps
By understanding the hacking threats hyperlinks pose and taking proactive…
Detecting Deepfakes—How They Are Created & How to Spot Them
Deepfakes can be detected by looking for telltale signs such…
How to Find Similar (Lookalike) Domain Names
Lookalike or “similar” domains are fraudulent domains that mimic…
So, What Does a Brand Protection Team Do Anyways?
Your brand is everywhere — on your website, across social…
Gray Market vs. Black Market: 5 Ways to Protect Your Business
The gray market and the black market are similar in…
Six Impersonation Attack Examples and How to Shield Your Business
Impersonation attacks are smarter and more deceptive than ever, with…
8 Ways to Prevent Typosquatting Attacks Targeting Your Business
Typosquatting as a type of URL spoofing is almost always…