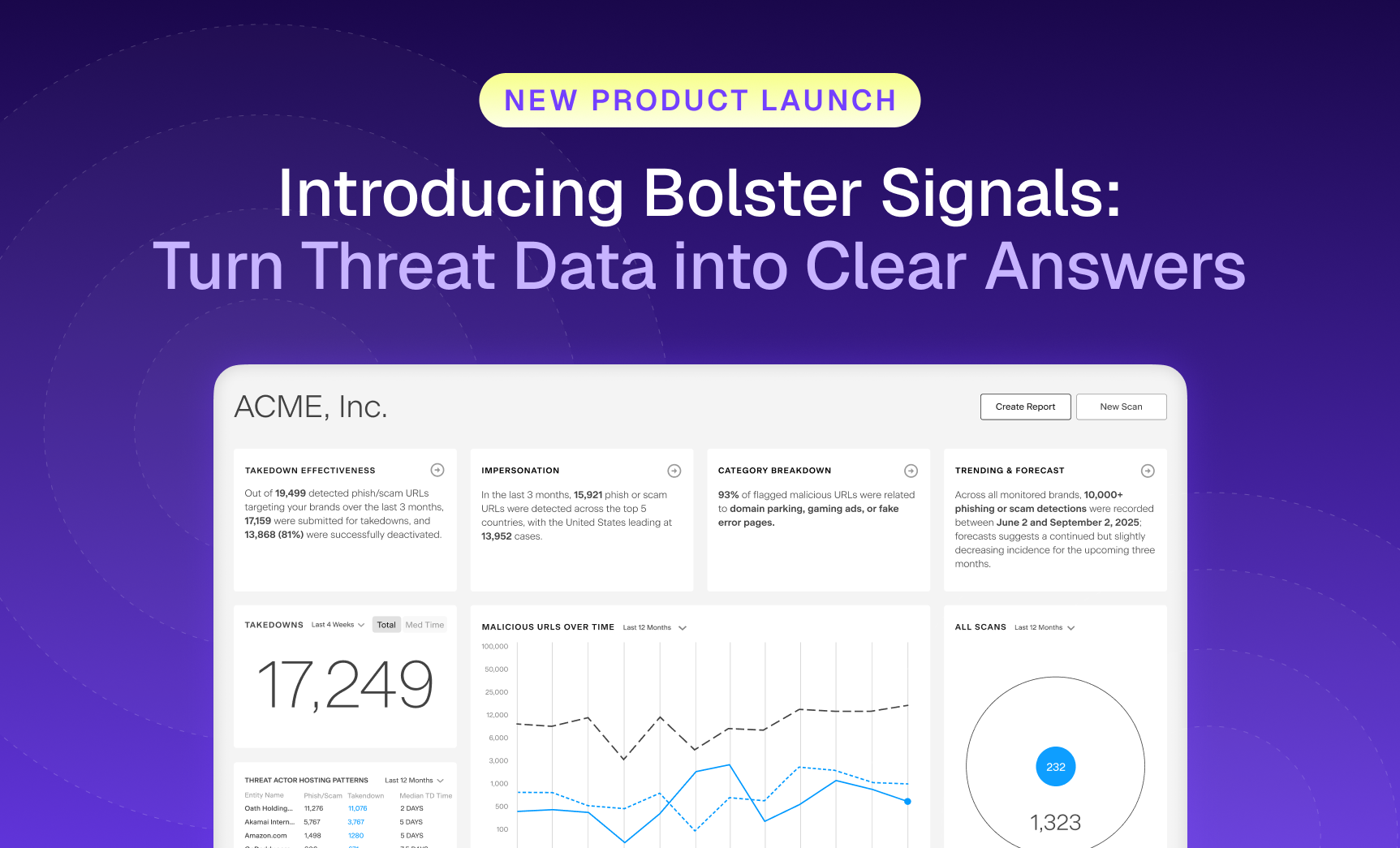
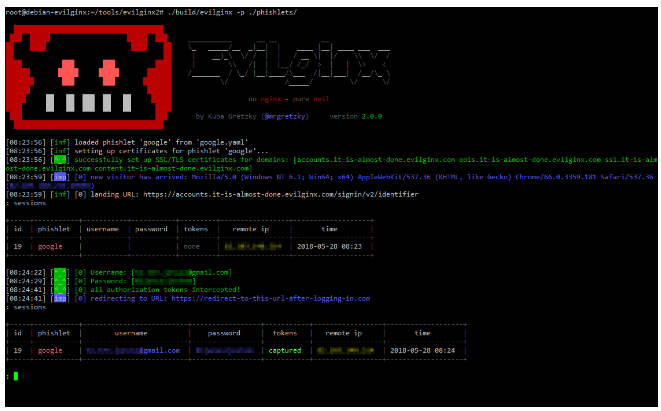
Security teams are flooded with more threat data than ever, and still struggle to see what matters most.…

The Bolster Blog
Thought provoking blogs discussing recent trends on digital risk protection services, phishing protection, threat intelligence, artificial intelligence, machine learning, brand protection and more!
Recent Posts
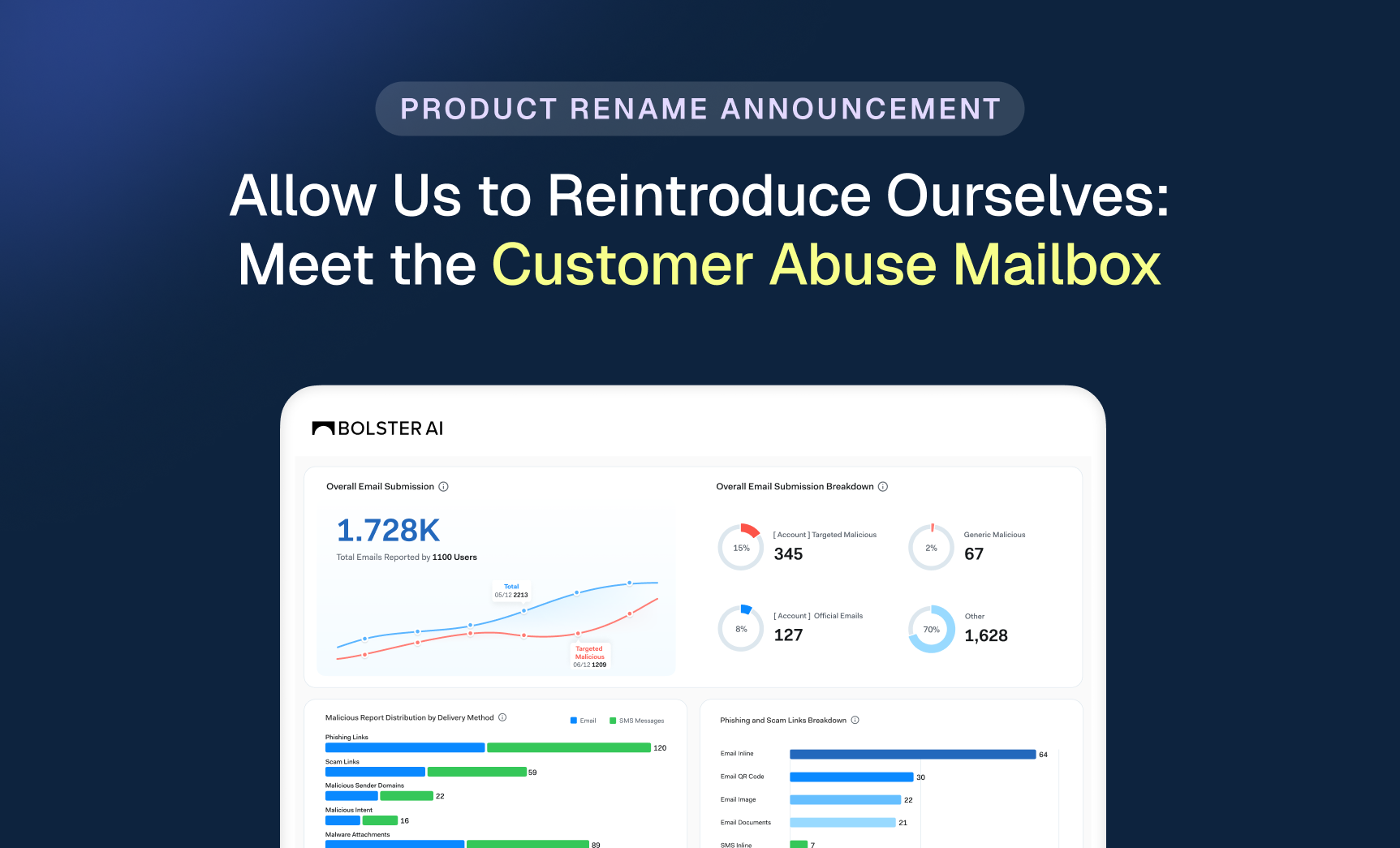
Allow Us to Reintroduce Ourselves: Meet the Customer Abuse Mailbox
Let’s clear something up. For a while, we referred to one of our most impactful features as “AI Security for Email.” While accurate in some.
Why AI-Generated Phishing Pages Are Harder to Detect (and How Bolster Stops Them)
Imagine clicking on what looks like your bank’s login page. The logo is crisp, the URL seems harmless at first glance, and even the support.

Buyer’s Guide: Purchasing a Brand Security Solution
Your brand is constantly under attack. To stay protected, you need an AI-powered brand security solution that keeps up with today’s AI-driven threats. Not sure what to look for? Use the Bolster AI Buyer’s Guide to evaluate your options.
Why Do Scammers Want You to Use the Telegram App?
Scammers want you to use Telegram because it gives them…
Exploring the Similar Worlds of Natural Language Processing (NLP) & Generative AI
Natural Language Processing (NLP) and Generative AI are reshaping cybersecurity,…
6 of the Best Anti-Phishing Software Choices to Protect Your Business
Phishing and online scam sites have become exceedingly sophisticated in…
Defining Subdomain Hijacking & How to Identify Subdomains at Risk
What is Subdomain Hijacking? Subdomain hijacking is an attacker having…
AI-Powered Fraud Detection 101: How to Uncover Cyber Attacks in 2025
Businesses are under constant pressure to stay ahead of digital…
How to Conduct a Website Takedown (The Hard Way), and How to Improve
If your business has any kind of digital presence in…
2025 Brand Protection Strategies: 12 Methods to Combat Evolving Digital Threats
Brand protection strategies need to evolve as quickly as the…
How to Avoid Fake CAPTCHA Scams That Initiate Malware
Online security measures like CAPTCHAs (Completely Automated Public Turing test…
The Click That Stole Holidays: Black Friday and Cyber Monday Scams Unmasked
The onset of Cyber Monday and Black Friday deals is…
Phishing & Online Scams Targeting the 2024 Election
As the 2024 U.S. presidential election draws near with discussions,…