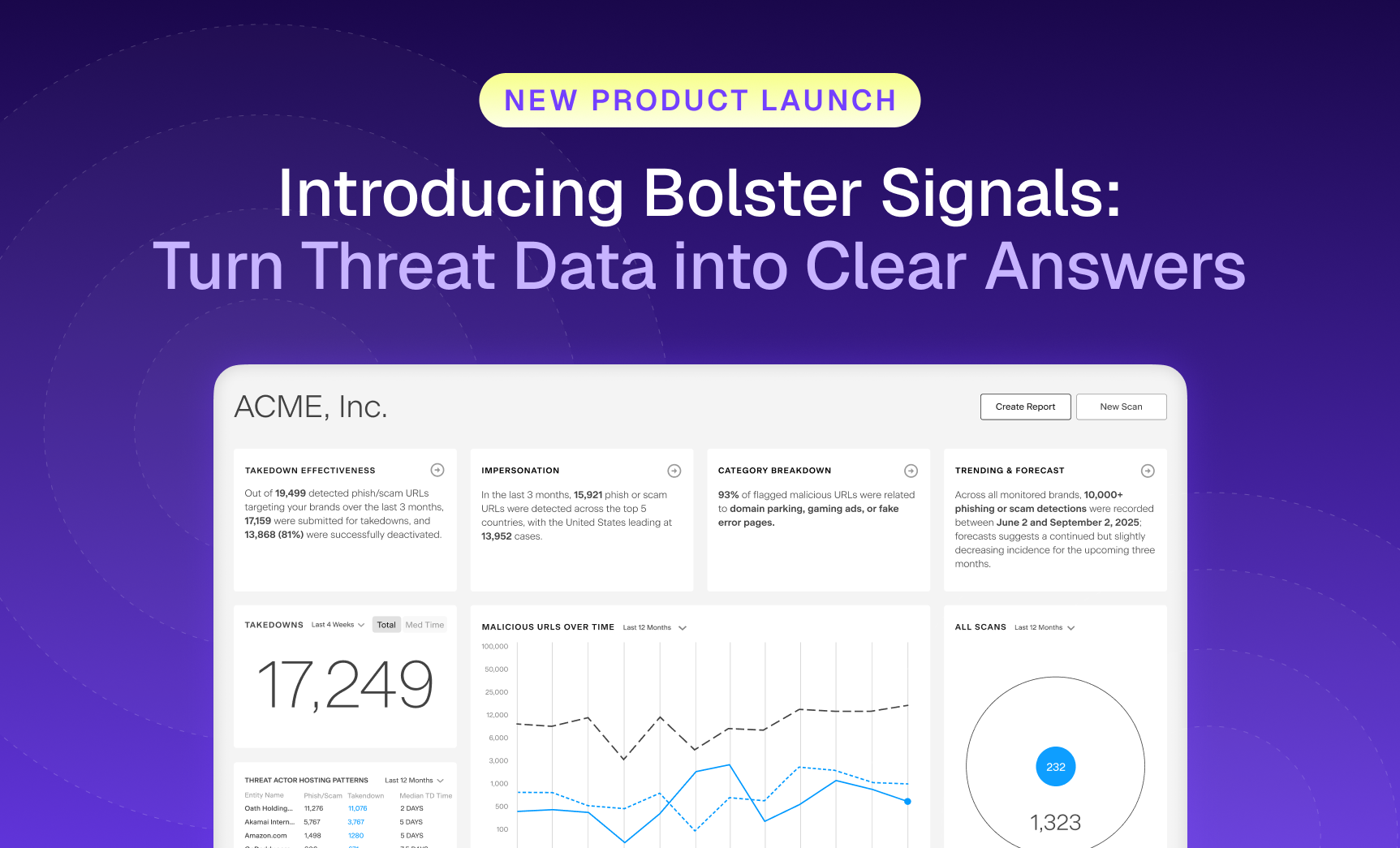
Security teams are flooded with more threat data than ever, and still struggle to see what matters most.…

The Bolster Blog
Thought provoking blogs discussing recent trends on digital risk protection services, phishing protection, threat intelligence, artificial intelligence, machine learning, brand protection and more!
Recent Posts
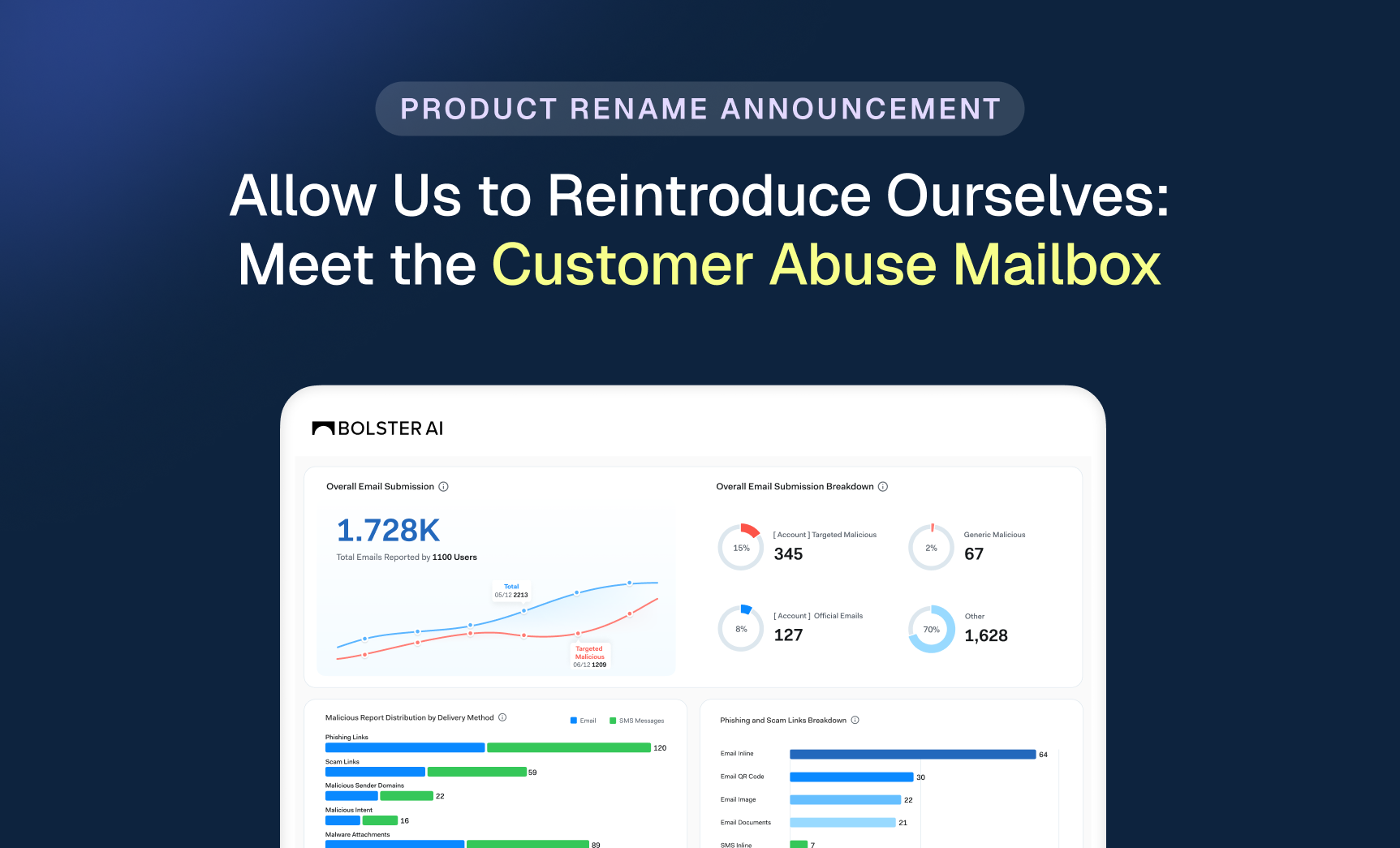
Allow Us to Reintroduce Ourselves: Meet the Customer Abuse Mailbox
Let’s clear something up. For a while, we referred to one of our most impactful features as “AI Security for Email.” While accurate in some.
Why AI-Generated Phishing Pages Are Harder to Detect (and How Bolster Stops Them)
Imagine clicking on what looks like your bank’s login page. The logo is crisp, the URL seems harmless at first glance, and even the support.

Buyer’s Guide: Purchasing a Brand Security Solution
Your brand is constantly under attack. To stay protected, you need an AI-powered brand security solution that keeps up with today’s AI-driven threats. Not sure what to look for? Use the Bolster AI Buyer’s Guide to evaluate your options.
Using Favicons to Discover Phishing & Brand Impersonation Websites
Almost every website on the internet, including phishing sites,…
Why Early Detection Matters in Phishing & Fraud Detection
Introduction Shashi and I started Bolster in 2017. Our…
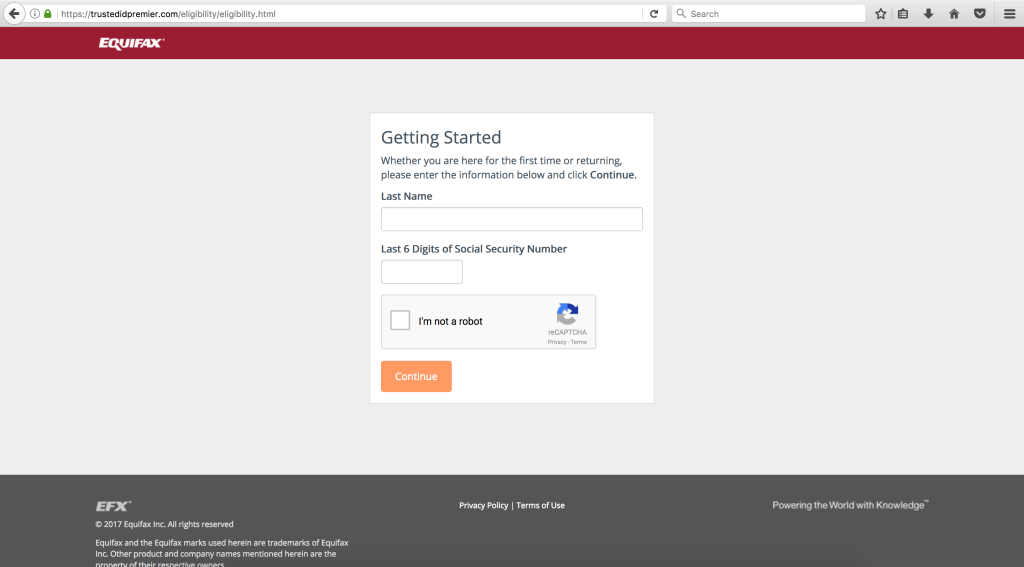
Equifax Data Breach: Look Out For These Suspicious Domains
Equifax, one of the three major credit bureaus in…
What Is Domain Spoofing and How to Stop It
What is Domain Spoofing? Domain spoofing is a type…
Fraudsters Joyride as Digital Business Skyrockets - Read More in our 2021 Report
Digital business is experiencing some serious liftoff as brands…
What are BEC (Business Email Compromise) Scams?
In 2021, FBI Internet Crime Complaint Center IC3, received…
What Is Domain Monitoring and Why You Need It
Typosquat domains are a popular tool in the attacker’s toolkit.…
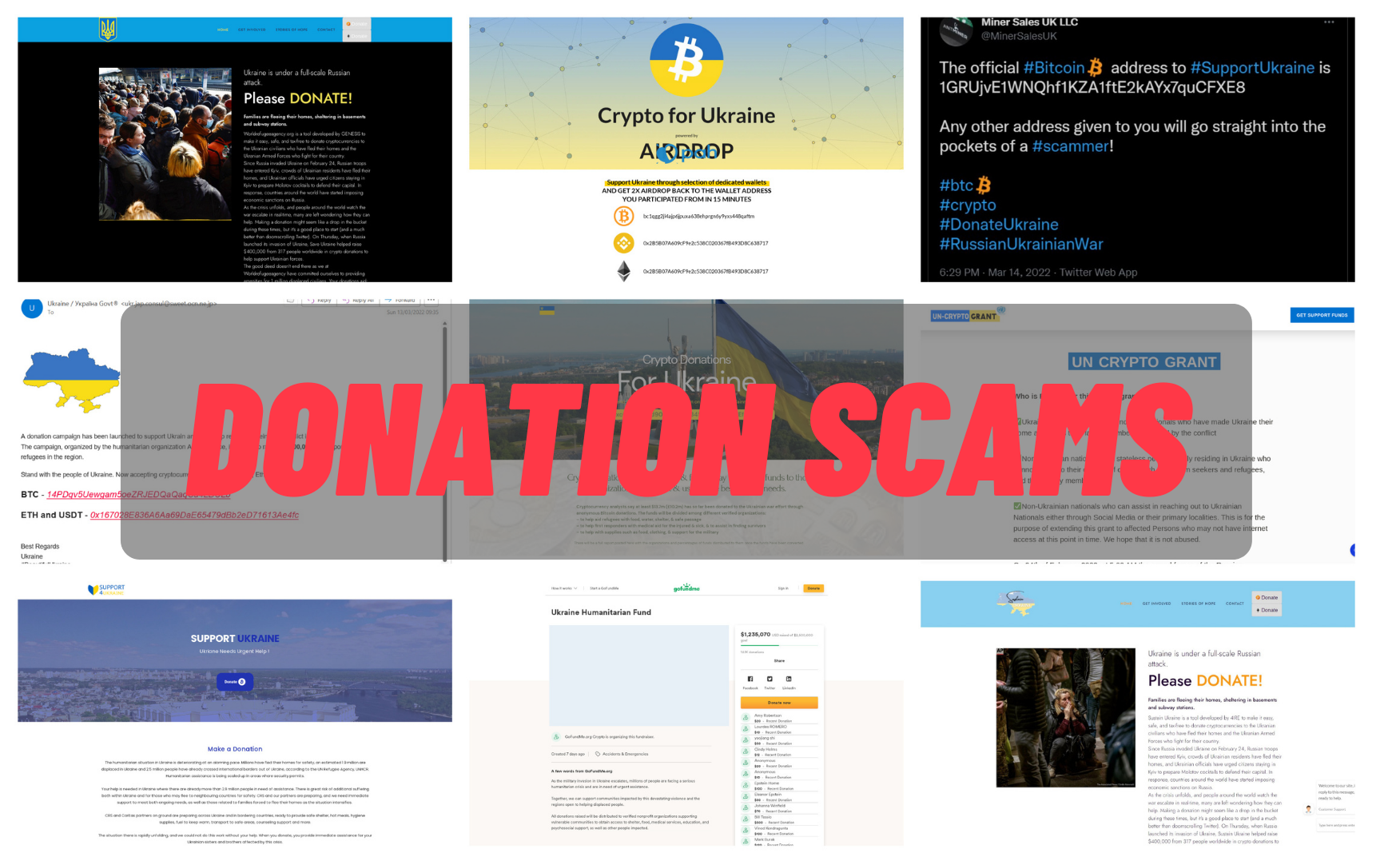
How Crypto Scammers Are Targeting Ukrainian Donation Campaigns
The Russian invasion of Ukraine on February 24th is…
Scaling Brand Protection for Enterprises with AI in 2023
Brand Protection for the Modern Enterprise It’s no secret that…
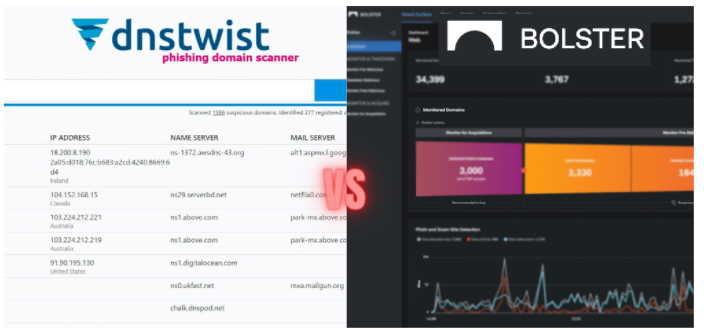
Comparing Bolster's Typosquatting Monitoring Tool to other OSINT Tools
What is Typosquatting? Cybercriminals register look-alike domains of well-known…