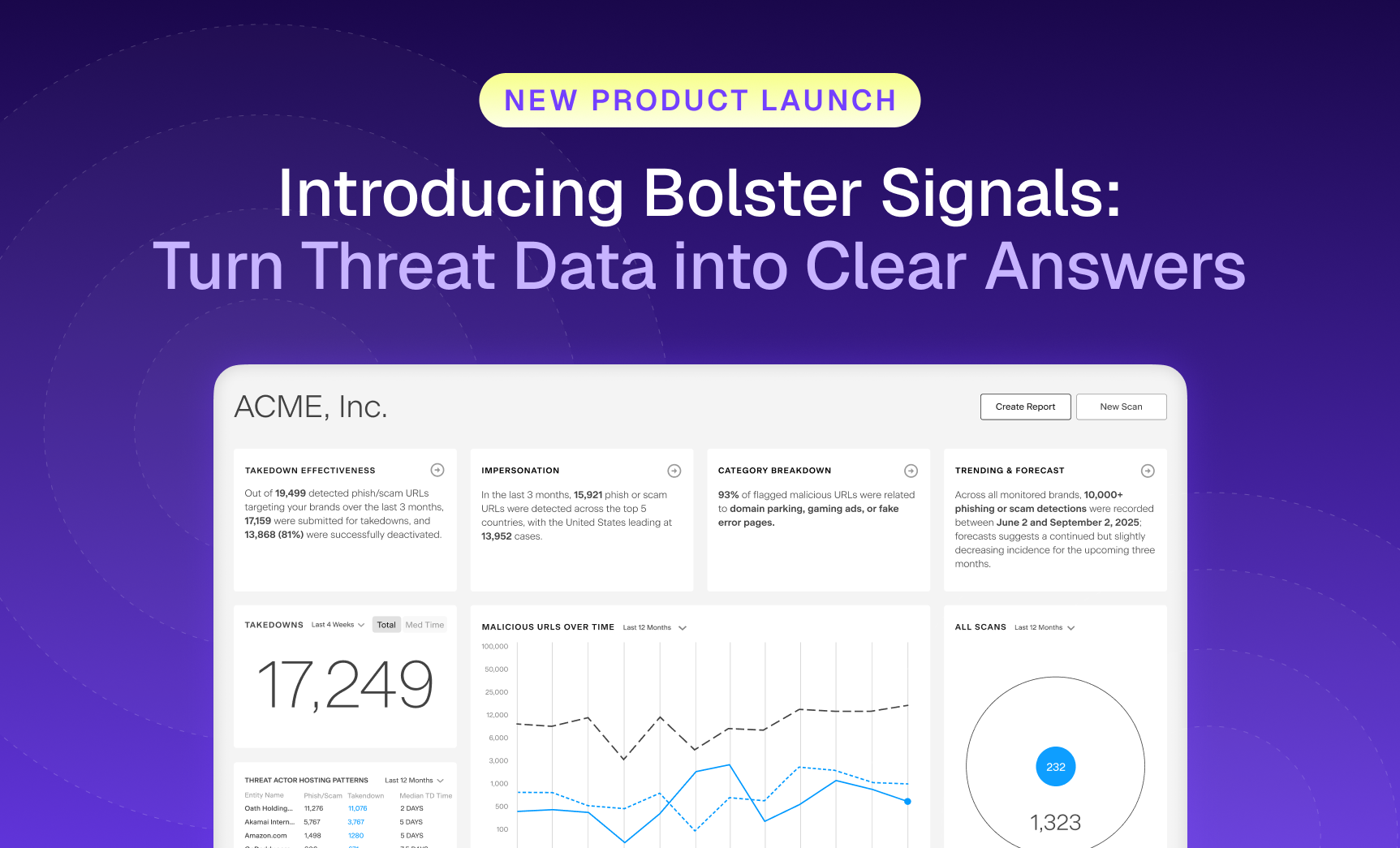
Security teams are flooded with more threat data than ever, and still struggle to see what matters most.…

The Bolster Blog
Thought provoking blogs discussing recent trends on digital risk protection services, phishing protection, threat intelligence, artificial intelligence, machine learning, brand protection and more!
Recent Posts
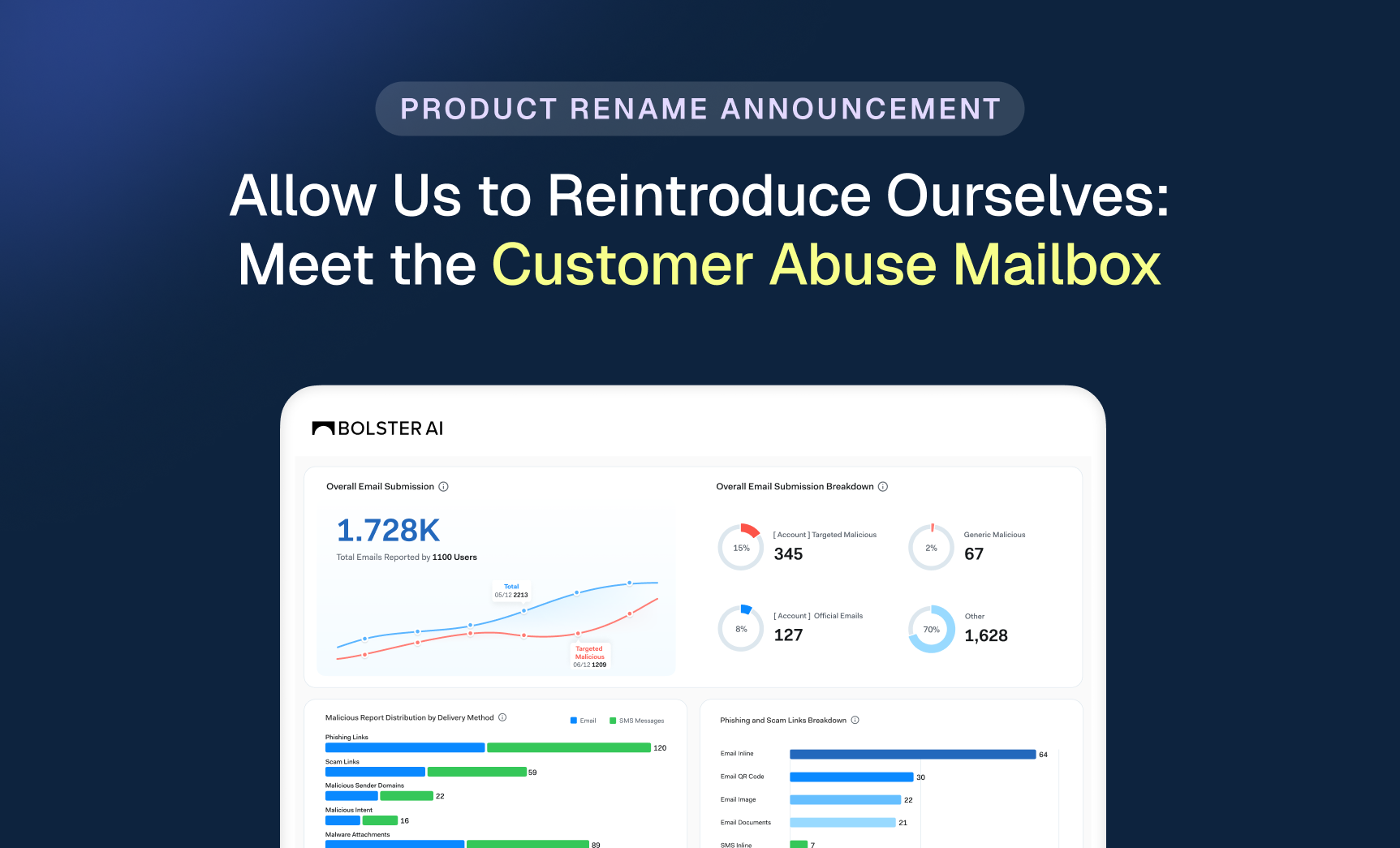
Allow Us to Reintroduce Ourselves: Meet the Customer Abuse Mailbox
Let’s clear something up. For a while, we referred to one of our most impactful features as “AI Security for Email.” While accurate in some.
Why AI-Generated Phishing Pages Are Harder to Detect (and How Bolster Stops Them)
Imagine clicking on what looks like your bank’s login page. The logo is crisp, the URL seems harmless at first glance, and even the support.

Buyer’s Guide: Purchasing a Brand Security Solution
Your brand is constantly under attack. To stay protected, you need an AI-powered brand security solution that keeps up with today’s AI-driven threats. Not sure what to look for? Use the Bolster AI Buyer’s Guide to evaluate your options.
The Importance of Automated Digital Risk Protection Services
Since the advent of the internet, digital risks have…
The Build vs. Buy Dilemma with Domain Risk Management
Domain risks are growing increasingly aggressive, and detrimental to businesses…
Evaluating Web Scraping, Crawling, and Automation with NodeJS Libraries
This blog is part 1 of a web scraping…
What’s Brand Protection Got to Do with External Attack Surface Management?
External attack surface management (EASM) encompasses a wide variety of…
Definitive Guide to Modern Brand Protection
Businesses are relying more and more on digital assets…
Account Takeover Fraud (ATO): 5 Steps for Protecting Your Customers
Account takeover fraud (ATO) is an attack where hackers compromise…
Phishing in the Metaverse: The New Reality of Brand Protection
The metaverse promises a new level of immersion and…
Copyright Infringement Examples: Lessons to Help You Protect Your Business
Copyright infringement is a fairly common technique for cyber criminals…
Real-world Phishing Attack Highlights Why Every CISO Needs to Protect Against Brand Impersonation
When researchers from Armorblox discovered a phishing attack from…
Monitoring for Copyright Infringement: 3 Steps to Defending Your Business
The case of Napster and the music industry demonstrated the…
Copyright Infringement: What It Is and How to Protect Your Business
As an IT security and risk management professional, understanding…
How to Avoid Online Shopping Scams on Amazon Prime Day
Prime Day is Amazon’s largest, most highly anticipated retail…