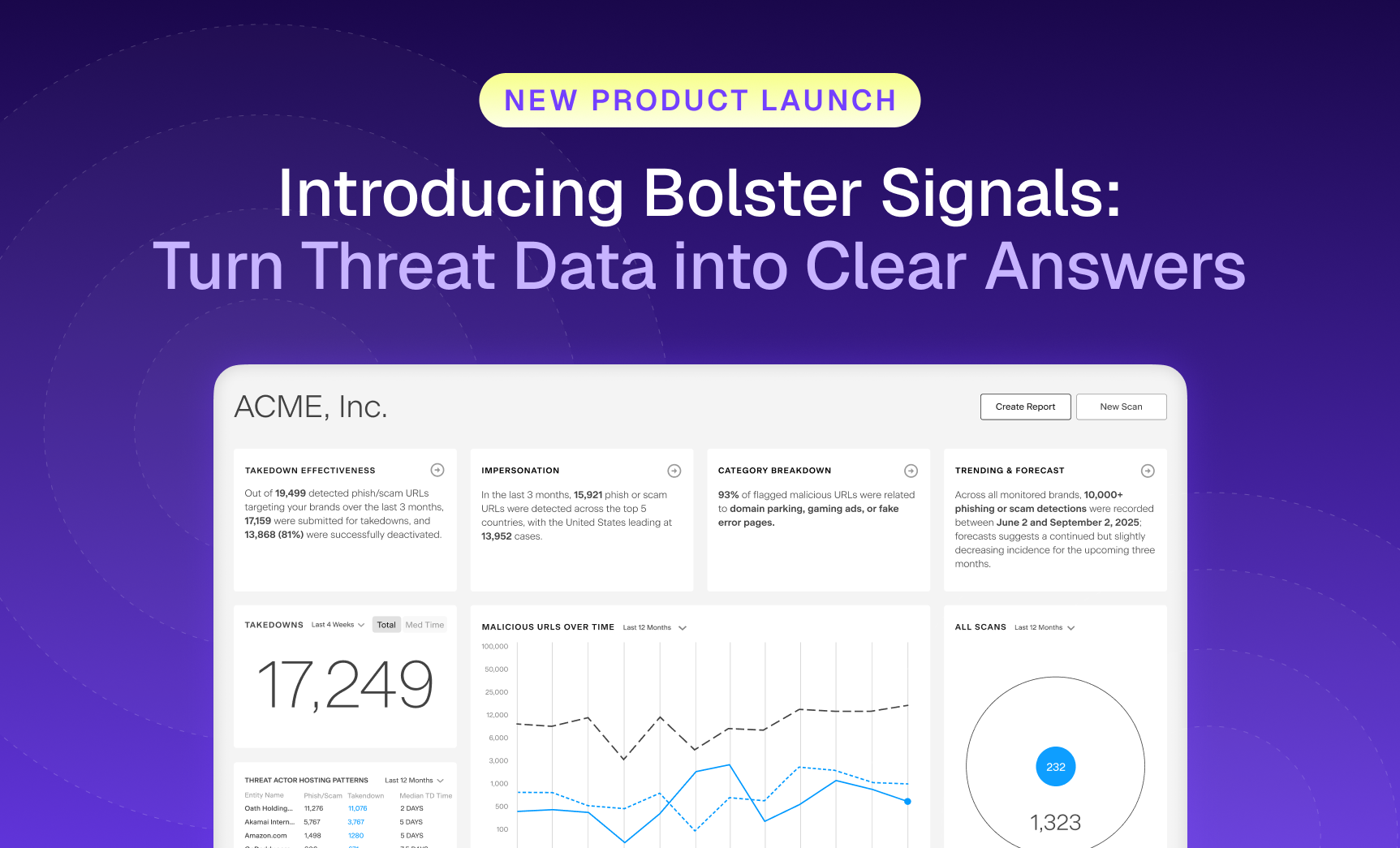
Security teams are flooded with more threat data than ever, and still struggle to see what matters most.…

The Bolster Blog
Thought provoking blogs discussing recent trends on digital risk protection services, phishing protection, threat intelligence, artificial intelligence, machine learning, brand protection and more!
Recent Posts
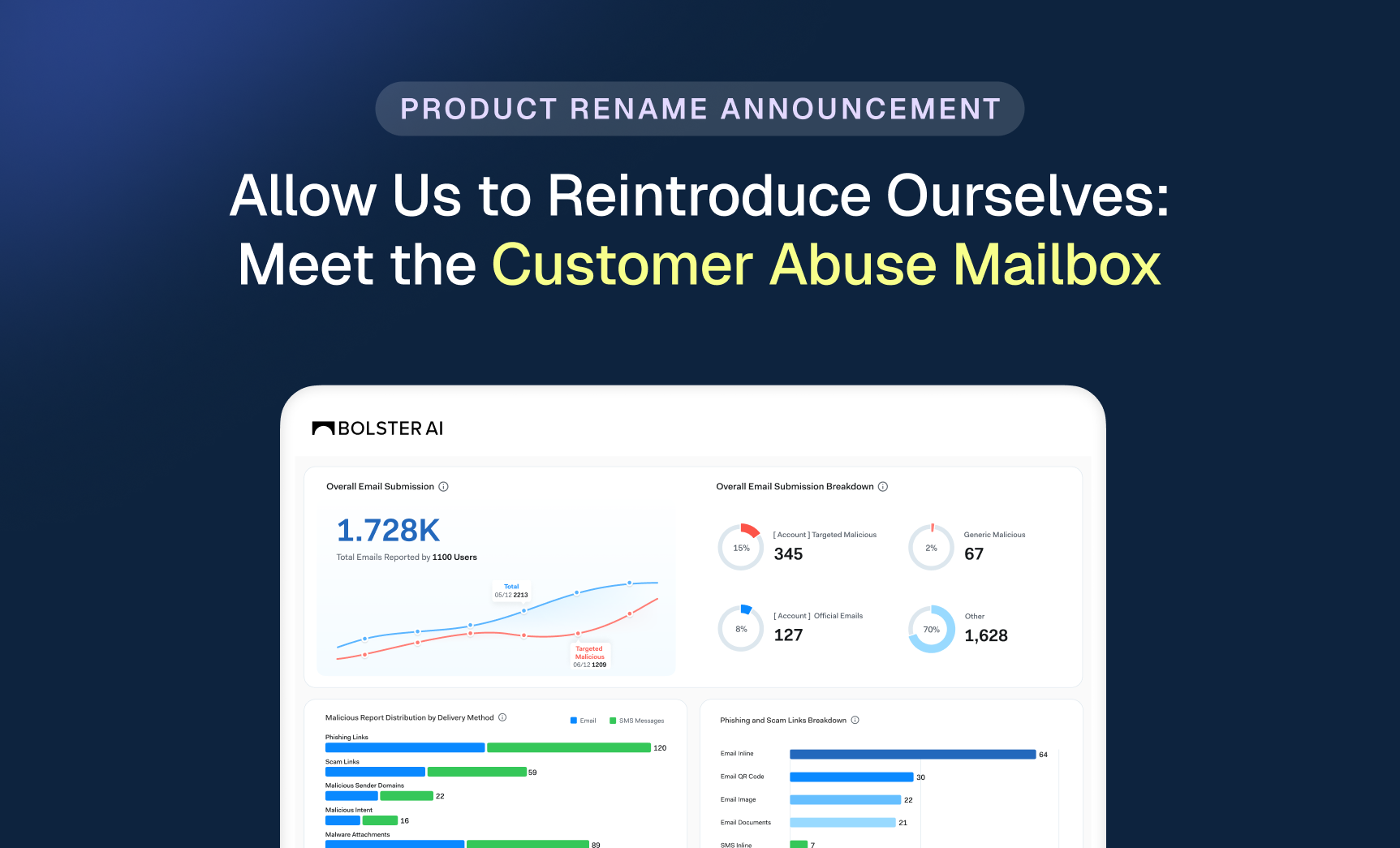
Allow Us to Reintroduce Ourselves: Meet the Customer Abuse Mailbox
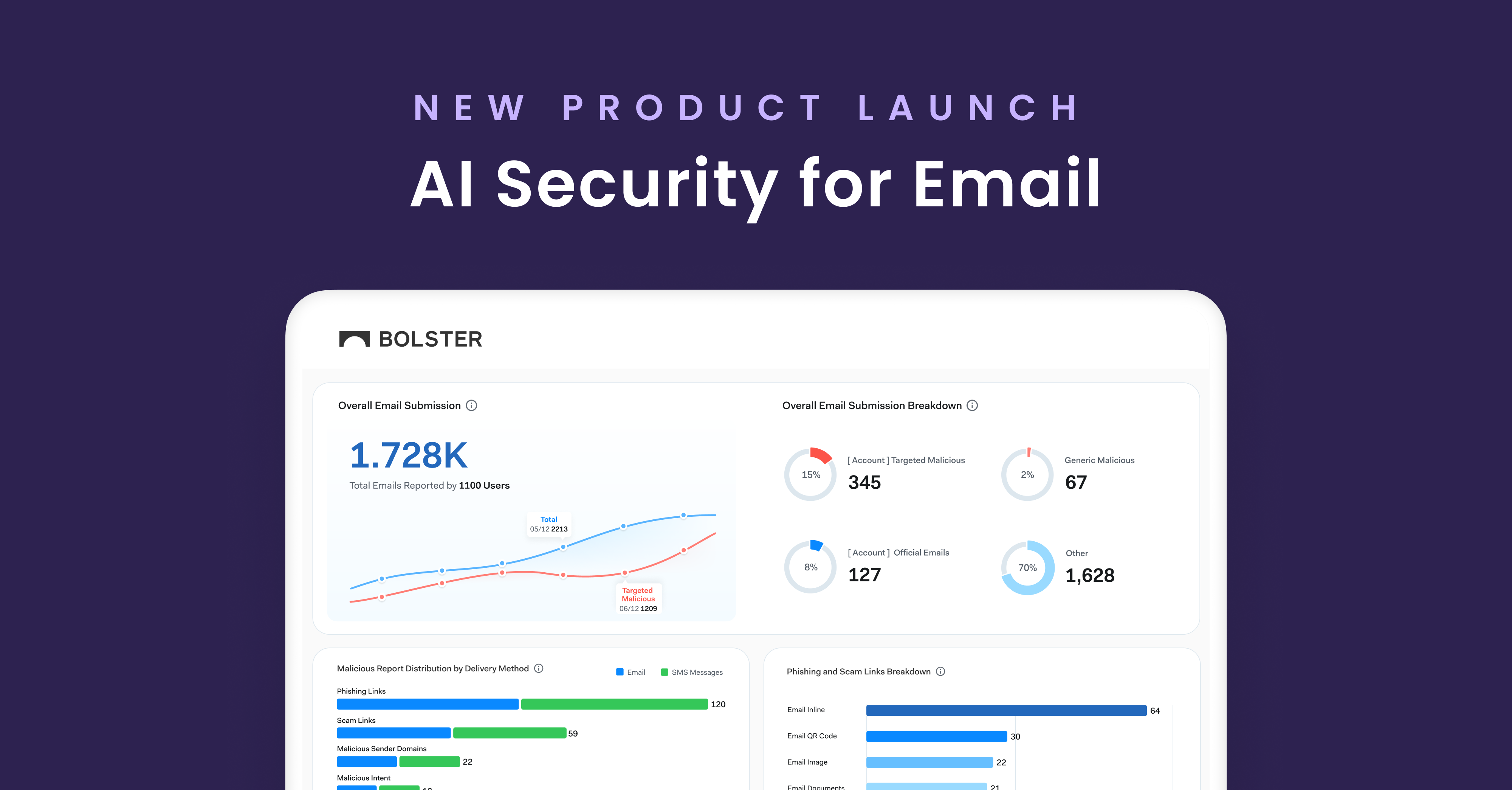
Let’s clear something up. For a while, we referred to one of our most impactful features as “AI Security for Email.” While accurate in some.
Why AI-Generated Phishing Pages Are Harder to Detect (and How Bolster Stops Them)
Imagine clicking on what looks like your bank’s login page. The logo is crisp, the URL seems harmless at first glance, and even the support.

Buyer’s Guide: Purchasing a Brand Security Solution
Your brand is constantly under attack. To stay protected, you need an AI-powered brand security solution that keeps up with today’s AI-driven threats. Not sure what to look for? Use the Bolster AI Buyer’s Guide to evaluate your options.
How to Safely Open a Suspicious Link in 5 Steps
By understanding the hacking threats hyperlinks pose and taking proactive…
How to Check for Spoofed Emails in Outlook
Spoofed emails often aim to steal sensitive information or spread…
6 of the Best Anti-Phishing Software Choices to Protect Your Business
Phishing and online scam sites have become exceedingly sophisticated in…
Beyond the Perimeter: Securing Your Brand with Customer-Focused Phishing Defense
In today’s digital landscape, email continues to be a primary…
Credit Union Scams: How Cybercriminals Are Targeting Small Credit Unions in the US
In recent months, Bolster’s research team has identified a surge…
Understanding Domain Reputation Attacks and How to Protect Your Brand
Without even defining the term, you could probably guess that…
Understanding Prepending and Its Role in Cybersecurity Attacks
Prepending involves adding data to the beginning of a string,…
In-Session Phishing is Becoming An Advanced Cybersecurity Threat
Phishing remains pretty much synonymous with “cyber attacks” as bad…
Cracking the Shield: Methods Hackers Use to Bypass MFA
Despite its apparent strength, Multi-Factor Authentication (MFA) is not immune…
Stopping Wire Fraud Scams Targeting VCs and Limited Partners
Everyone in the world knows if you need money for…