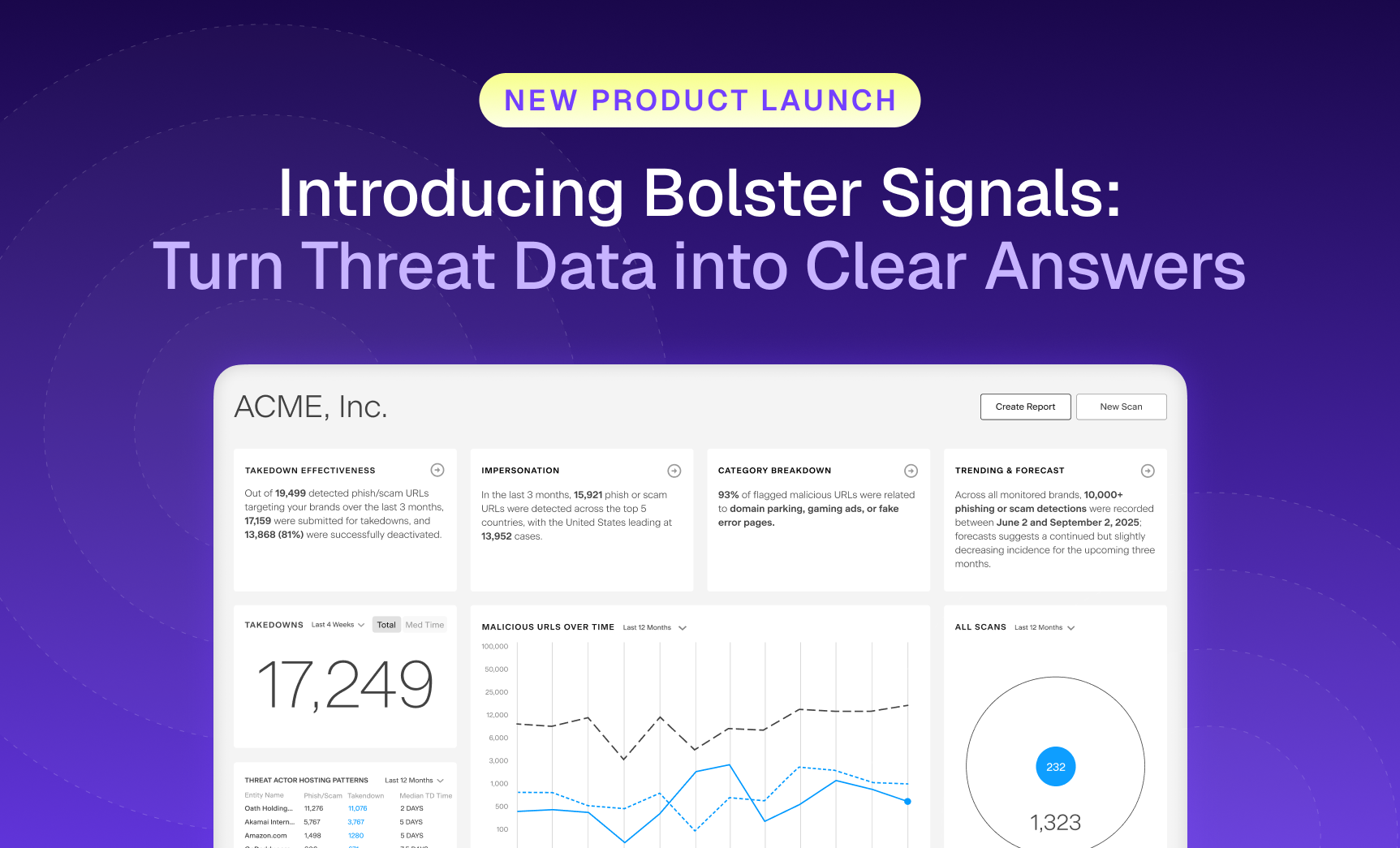
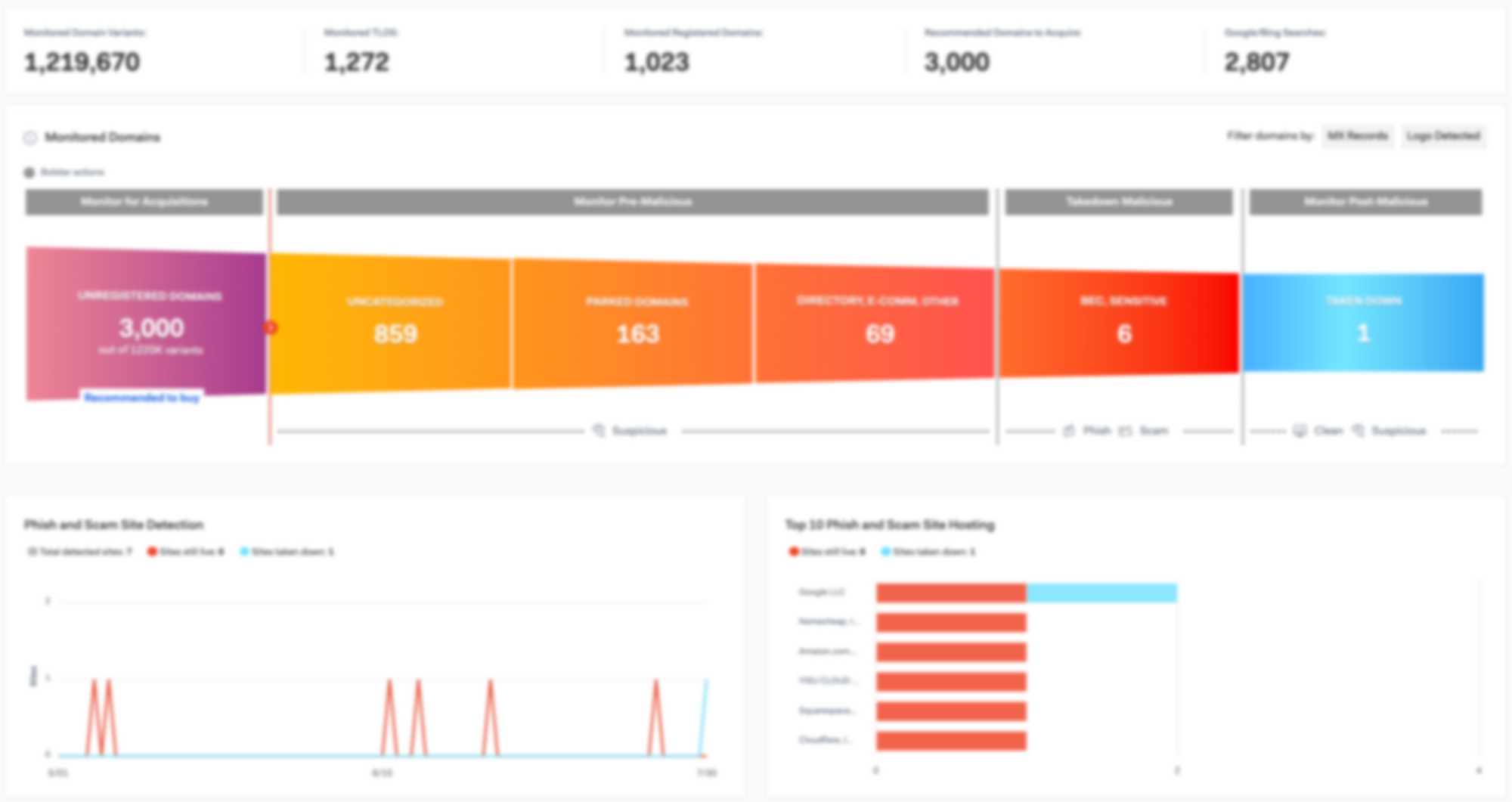
Security teams are flooded with more threat data than ever, and still struggle to see what matters most.…

The Bolster Blog
Thought provoking blogs discussing recent trends on digital risk protection services, phishing protection, threat intelligence, artificial intelligence, machine learning, brand protection and more!
Recent Posts
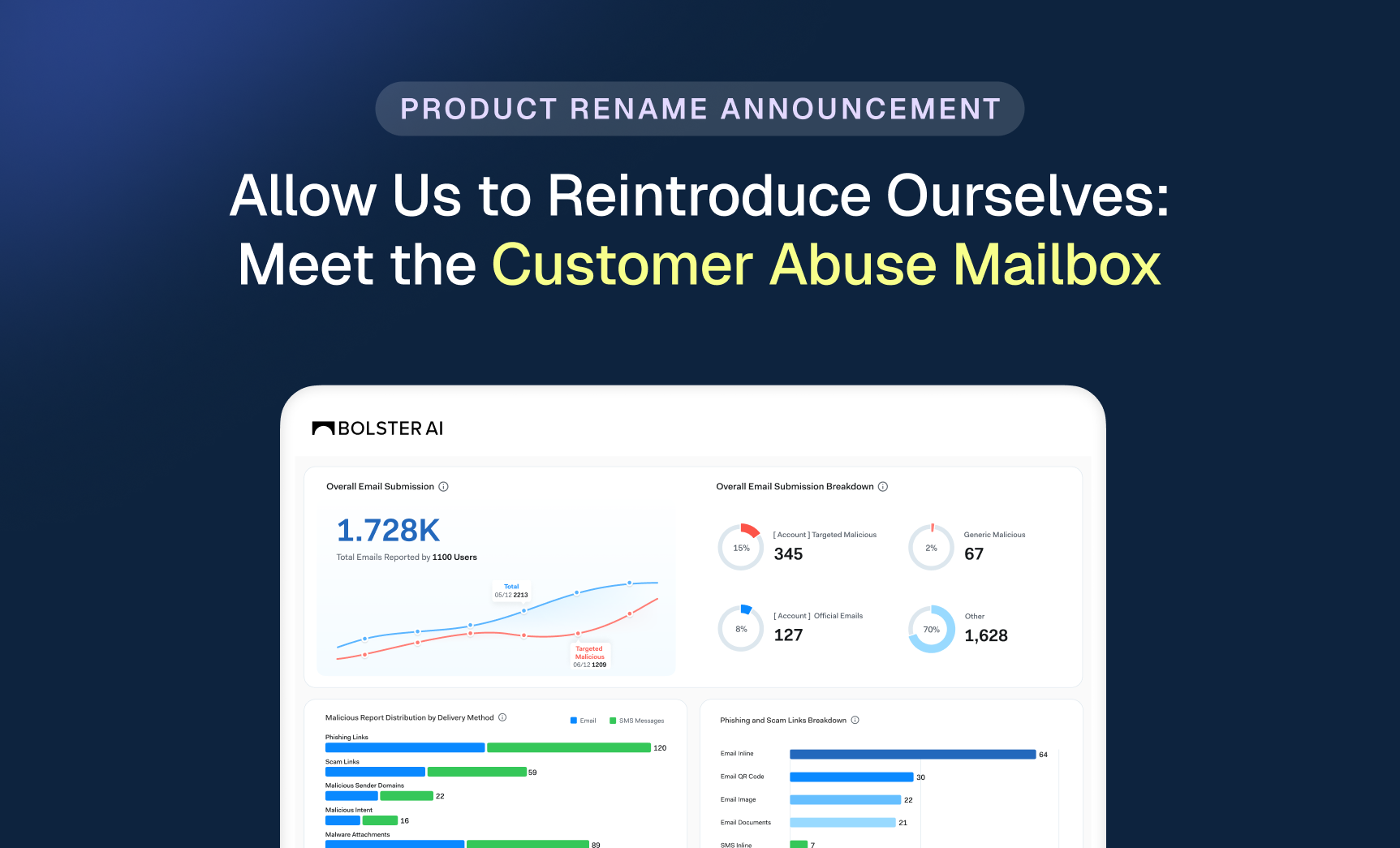
Allow Us to Reintroduce Ourselves: Meet the Customer Abuse Mailbox
Let’s clear something up. For a while, we referred to one of our most impactful features as “AI Security for Email.” While accurate in some.
Why AI-Generated Phishing Pages Are Harder to Detect (and How Bolster Stops Them)
Imagine clicking on what looks like your bank’s login page. The logo is crisp, the URL seems harmless at first glance, and even the support.

Buyer’s Guide: Purchasing a Brand Security Solution
Your brand is constantly under attack. To stay protected, you need an AI-powered brand security solution that keeps up with today’s AI-driven threats. Not sure what to look for? Use the Bolster AI Buyer’s Guide to evaluate your options.
Six Impersonation Attack Examples and How to Shield Your Business
Impersonation attacks are smarter and more deceptive than ever, with…
8 Ways to Prevent Typosquatting Attacks Targeting Your Business
Typosquatting as a type of URL spoofing is almost always…
Securing Your Python Projects from PyPI Supply Chain Attacks
The cybersecurity landscape is growing more complex by the day,…
Digital Risk Monitoring Importance is Growing Faster Than Ever
In a digital landscape that seems to be changing daily…
How to Avoid Online Shopping Scams on Amazon Prime Day
Prime Day is Amazon’s largest, most highly anticipated retail…
Embedded Secrets in Webpage DOMs (and How to Use this Data to Protect Your Assets)
The dangerous impact of typosquat domains, and how frequently…
How to Remove a Typosquat Domain Targeting Your Company, Even When the Registrar Won’t Comply
Typosquat domains can damage not only an organization’s finances,…
Identifying SSL Certificate Scams & Importance of Monitoring for Brand's Identity
Phishing and scam websites often use SSL certificates to…
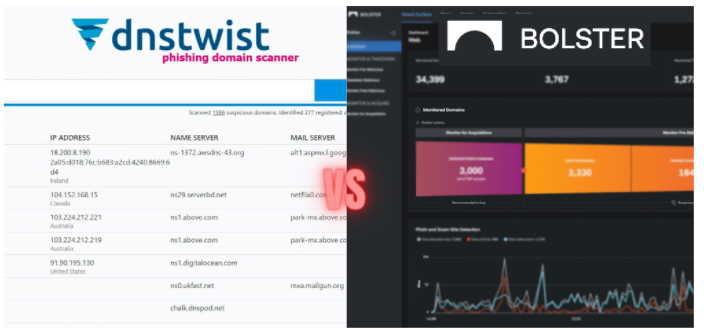
Comparing Bolster's Typosquatting Monitoring Tool to other OSINT Tools
What is Typosquatting? Cybercriminals register look-alike domains of well-known…
What Every CISO Should Do to Fight Typosquat Attacks
Microsoft recently secured a court order to takedown ‘homoglyph’ domains…
NFT Scams Part 2: Typosquatting Attacks targeting NFT marketplace users
Before we get started, there are a couple of terms…